In this article:
Foresight Analytics Platform Authentication
Foresight Analytics Platform provides several authentication methods. Authentication method is selected depending on the required security measures during repository access setup.
User credentials can be checked on DBMS server and/or in Foresight Analytics Platform.
The following basic authentication types are available:
Password. Default value. The user is authenticated by means of specifying user name and password explicitly.
Integrated domain. The user is authenticated by means of specifying domain user name and password (the current OS account).
Domain. The user is authenticated by means of specifying domain, user name and password explicitly.
Availability of basic authentication types depends on the DBMS in use:
| DBMS type \ Authentication type | Password | Integrated domain | Domain |
| Oracle |  |
 |
 |
| Microsoft SQL Server |  |
 |
 |
| Microsoft SQL Server (ODBC) |  |
 |
 |
| PostgreSQL |  |
 |
 |
| SQLite |  |
 |
 |
| WEB Service |  |
 |
 |
Designations:
 - authentication type is available in Linux OS and Windows OS.
- authentication type is available in Linux OS and Windows OS.
 - authentication type is available only in Windows OS.
- authentication type is available only in Windows OS.
 - authentication type is available.
- authentication type is available.
There are additional authentication types besides the mentioned ones:
Two-factor authentication. It is used together with any basic authentication type.
Built-in authorization. It is used together with any basic authentication type. Simultaneous use of built-in authorization with domain or integrated domain authentication is available only when working with PostgreSQL DBMS.
The following authentication types are available in the web application besides the basic ones:
External services. It supports the services working via the OAuth 2.0 and OpenID Connect protocols, the services returning JWT token or adding HTTP headers with user information to queries.
Guest login. It is used to get familiar with web application work.
Password Authentication
The user is authenticated using user name and password explicitly.
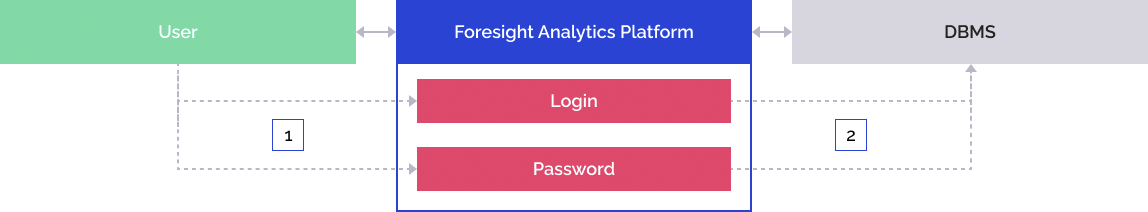
The user enters user name and password in the login dialog box of Foresight Analytics Platform:
Foresight Analytics Platform addresses DBMS by means of the given user name and password.
To use password authentication, set up password policy in the security manager.
Integrated Domain Authentication
Integrated domain authentication is similar to standard domain authentication, except the domain user, under whom the operating system is logged in, is used for authorization.
When working with PostgreSQL DBMS, integrated domain authentication is executed using Kerberos authentication. This mechanism can be activated optionally in additional parameters of repository connection.
To work according to Kerberos protocol, install MIT Kerberos on a client computer (not included into software package of Foresight Analytics Platform).
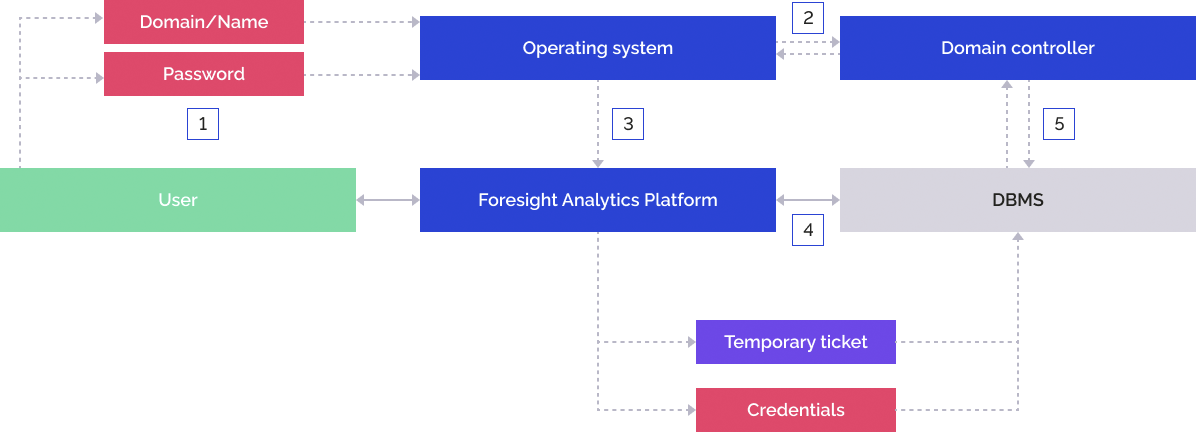
The user enters domain user name and password on the operating system login.
The operating system addresses the domain controller, the domain controller checks correctness of the specified data and returns the temporary ticket to the operating system.
The operating system sends the specified credentials and the temporary ticket to Foresight Analytics Platform. The login dialog box does not display the User Name and Password boxes:

Foresight Analytics Platform sends the credentials and the temporary ticket to the DBMS server.
DBMS addresses the domain controller, the domain controller checks correctness of the specified data and grants Foresight Analytics Platform permission to connect under the domain user by means of a temporary ticket.
To use integrated domain authentication, one should add domain users or groups in the security manager. When working in the web application, set up integrated domain authentication depending on the web server:
If Apache2 web server is used, see the Setting Up Domain/Integrated Domain Authentication on Apache2 Web Server section.
If ASP.NET web server is used, see the Setting Up Domain/Integrated Domain Authentication on ASP.NET web server section.
If Java web server is used, see the Setting Up Domain/Integrated Domain Authentication on Java Web Server section.
Domain Authentication
The user is authenticated by means of specifying domain, user name and password explicitly. The following directory services are supported: Active Directory, OpenLDAP. For details about interaction between Foresight Analytics Platform and domain directory services, see the Working with Directory Services section. Domain authentication is always executed using Kerberos authentication on DBMS side.
Domain authentication is similar to password authentication for the end user, but it facilitates user administration on using domain controllers.
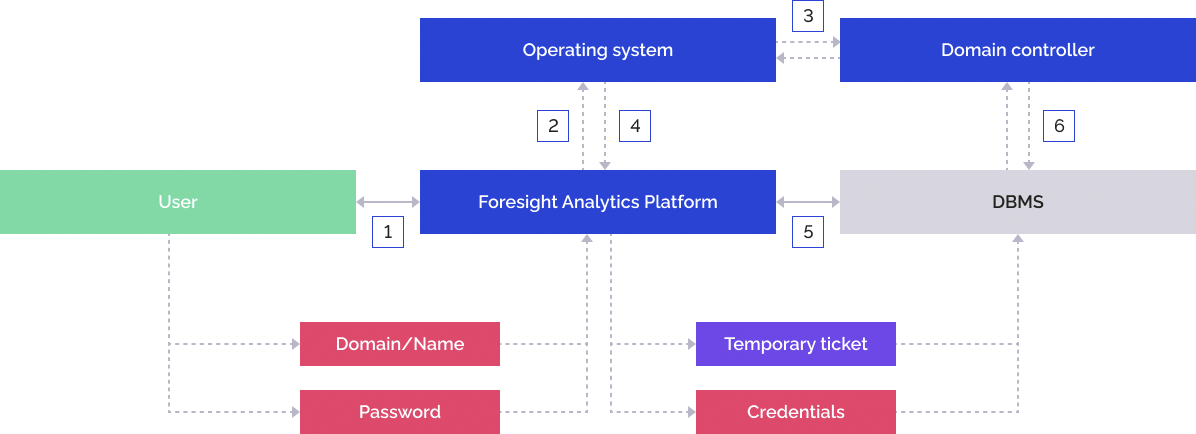
The user enters domain user name in the format: domain\name and password in the login dialog box of Foresight Analytics Platform:
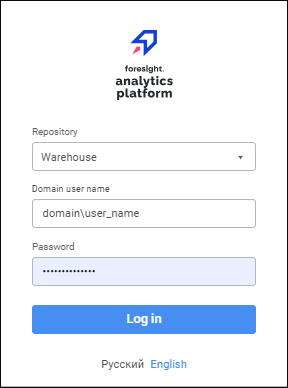
Foresight Analytics Platform sends the specified credentials to the operating system.
The operating system addresses the domain controller, the domain controller checks correctness of the specified data and returns the temporary ticket to the operating system.
The operating system returns the temporary ticket to Foresight Analytics Platform.
Foresight Analytics Platform sends the specified credentials and the temporary ticket to the DBMS server.
DBMS addresses the domain controller, the domain controller checks correctness of the specified data and grants Foresight Analytics Platform permission to connect under the domain user by means of a temporary ticket.
To use domain authentication, one should add domain users or groups in the security manager. When working in the web application, set up domain authentication depending on the web server:
If Apache2 web server is used, see the Setting Up Domain/Integrated Domain Authentication on Apache2 Web Server section.
If ASP.NET web server is used, see the Setting Up Domain/Integrated Domain Authentication on ASP.NET web server section.
If Java web server is used, see the Setting Up Domain/Integrated Domain Authentication on Java Web Server section.
Two-Factor Authentication
The user is authenticated using any basic authentication type or user certificate.
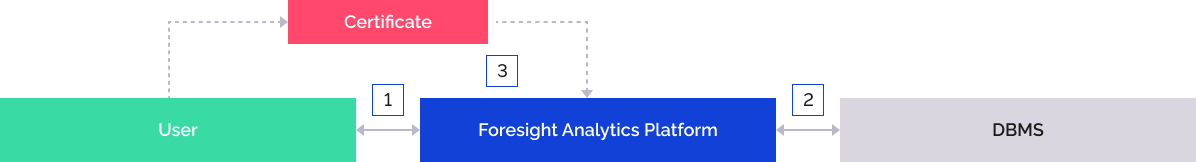
The user executes basic authentication in Foresight Analytics Platform.
Foresight Analytics Platform addresses DBMS by means of the given user name and password.
The user grants Foresight Analytics Platform the certificate after executing a query and gets access to repository if the certificates match.
To use two-factor authentication, see the Setting Up Two-Factor Authentication section.
Built-In Authorization
User authentication and access to DBMS data is executed under the built-in administrator and is used together with password authentication type by default. User permissions are checked at the level of Foresight Analytics Platform. Administrator credentials are stored in encrypted form.
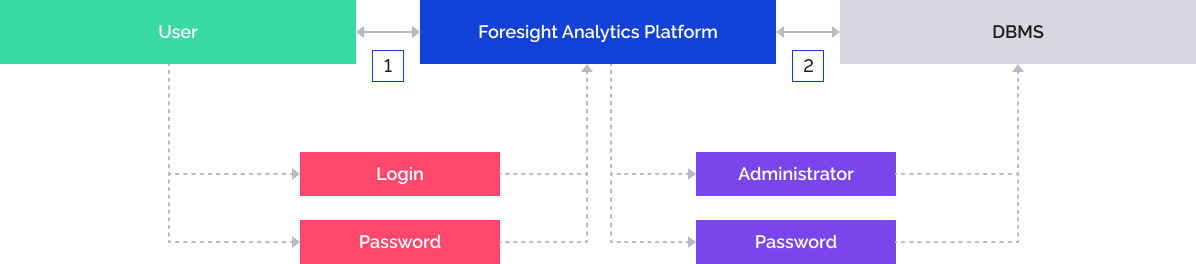
The user enters login and password to Foresight Analytics Platform.
Foresight Analytics Platform checks user permissions and addresses the DBMS by means of the built-in administrator user credentials.
Simultaneous use built-in authorization with domain or integrated domain authentication is available when working with PostgreSQL DBMS. The scheme of interaction between built-in authorization element is similar to scheme of interaction between elements and external service.
To use built-in authorization, see the Setting Up Built-In Authorization section.
External Services
The user is authorized in the repository after the user was authenticated in an external service. In this authorization type DBMS connection is executed using a technological account. Technological account is an account used for connection to and communication with DBMS during user authentication via external services. In the security manager one should create one or several users who will be used as technological accounts. Each technological account credentials should be saved using the PP.Util utility.
The user is authenticated by means of specifying an account of the services that support the OAuth 2.0 or OpenID Connect protocol.
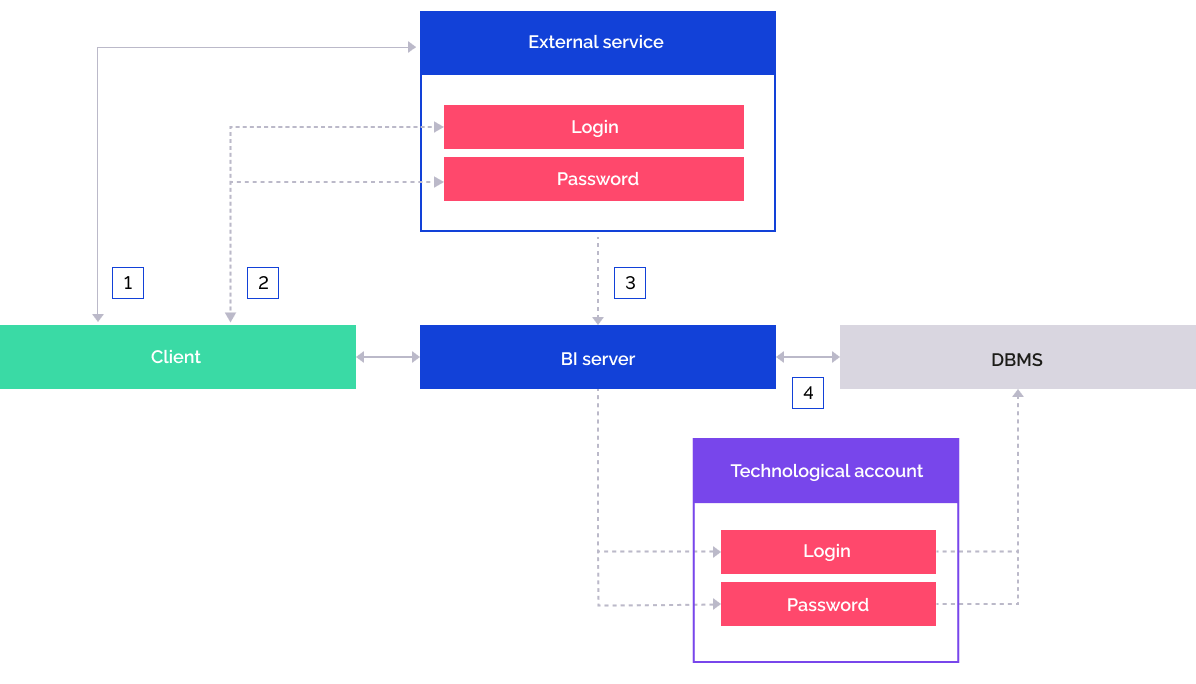
The user selects the repository configured to work with an external service:

The user is redirected to an external authorization service where the user enters login and password.
The user is authorized on the external service and BI server gets necessary information about the user.
The BI server addresses the DBMS by means of the previously saved technological account.
When logging in to repository using JWT token, after the user is authenticated in the external service, BI server queries should be added with headers containing JWT token with user information. When the repository connection opens, the user information is obtained from the JWT token.
NOTE. Interaction between the external authentication service and the proxy server, which adds headers to queries, is not described in this help and can be implemented at administrator's discretion. The trust between the BI server and the proxy server, which adds headers to queries, is provided by checking with JWT token signature.
If the external service's user account is contained in the security manager, the repository connection is established and the object navigator opens using this user account.
If the external service's user account is not contained in the security manager, a temporary user is created and added to groups from the list specified in the corresponding attribute of the JWT token. If the attribute containing the list of groups is not set, the temporary user is added to the USERS built-in group.
NOTE. The temporary user cannot be included in the ADMINISTRATORS built-in group.
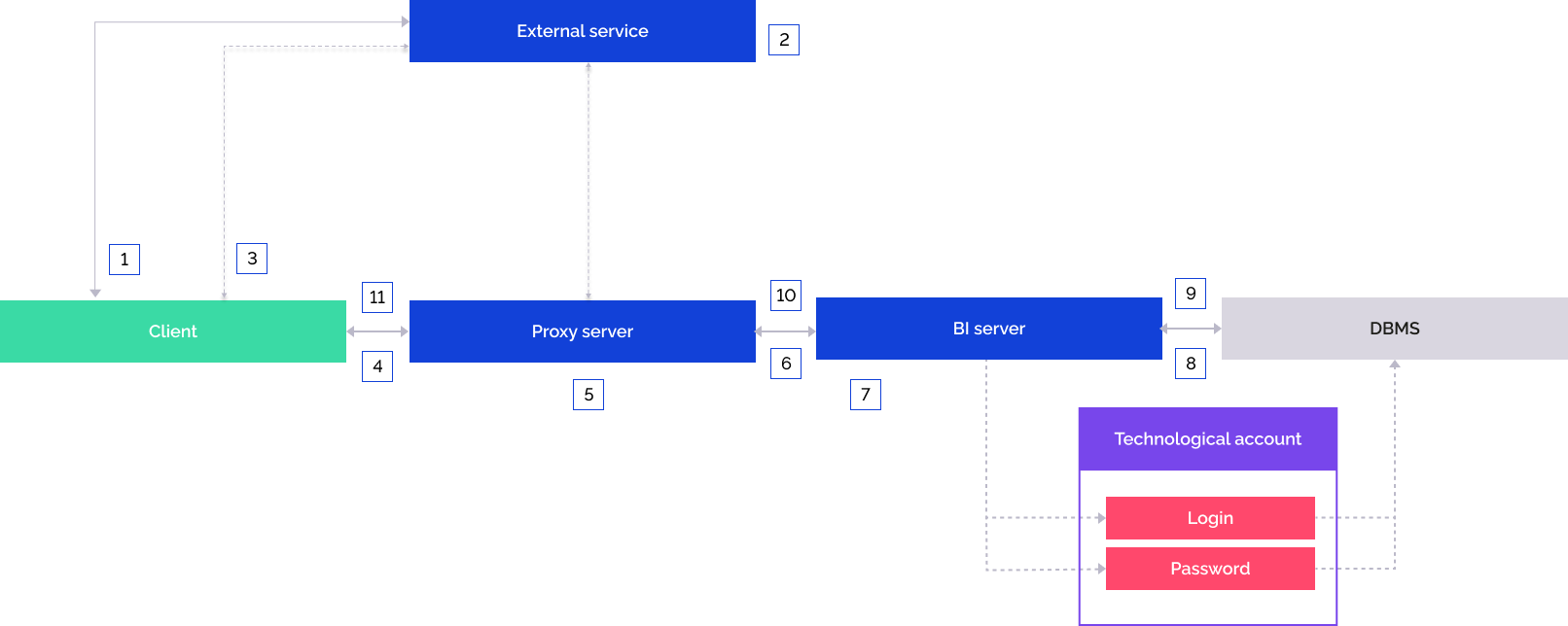
The user opens the external authentication service.
The user is authenticated in the external service.
If the authentication is successful, the external service redirects the user to the web application page and includes repository identifier to the URL.
The web application redirects queries to the proxy server.
Queries are appended with headers containing JWT token with user information on the proxy server.
The appended query is sent to the BI server.
The BI server checks JWT token signature. If the check is successful, user information is obtained from the JWT token.
The BI server connects to the DBMS using a technological account.
If the external service's user account is contained in the security manager, the repository connection is established and the object navigator opens under this user.
If the external service's user account is not contained in the security manager, a temporary user is created and added to groups from the list specified in the corresponding attribute of the JWT token. If the attribute is not set, the temporary user is added to the USERS built-in group.The repository connection opens.
The web application page is displayed, to which the user was redirected.
When logging in to repository using HTTP headers, after the user is authenticated in the external service, BI server queries should be added with HTTP headers with user information.
An mTLS connection should be set up between the proxy server that establishes BI server connection and adds includes headers to queries and the BI server.
NOTE. Interaction between the external authentication service and the proxy server is not described in this help and can be implemented at administrator's discretion.
Trust between the BI server and the proxy server is established by comparing certificate's digital fingerprint specified in the description of external service settings in the ExtService section of the settings.xml file/in the registry and certificate's digital fingerprint obtained from the proxy server during establishing mTLS connection with the BI server.
If the external service's user account is contained in the security manager, the repository connection is established and the object navigator opens using this user account.
If the external service's user account is not contained in the security manager, a temporary user is created and added to groups from the list specified in the corresponding header. If the header containing the list of groups is not set, the temporary user is added to the USERS built-in group.
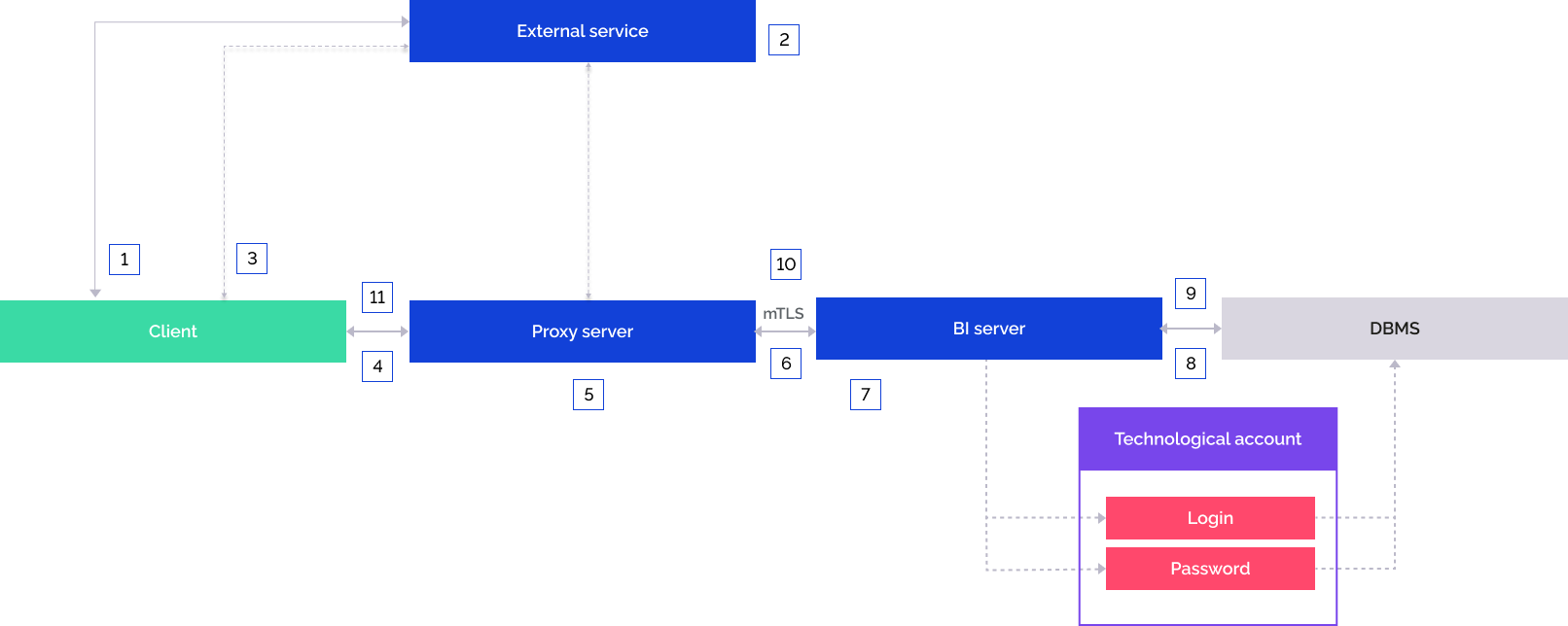
The user opens the external authentication service.
The user is authenticated in the external service.
If the authentication is successful, the external service redirects the user to the web application page and includes repository identifier to the URL.
The web application redirects queries to the proxy server.
Queries are appended with HTTP headers with user information on the proxy server.
The appended query is sent to the BI server. An mTLS connection should be set up in advance between the proxy server and the BI server.
The BI server compares the certificate's digital fingerprint of the proxy server specified in description of external service settings in the ExtService section of the settings.xml file/registry and the digital fingerprint obtained from the proxy server during establishing mTLS connection with the BI server. If the check is successful, user information is obtained from HTTP headers.
The BI server connects to the DBMS using a technological account.
If the external service's user account is contained in the security manager, the repository connection is established and the object navigator opens under this user.
If the external service's user account is not contained in the security manager, a temporary user is created and added to groups from the list specified in the corresponding header. If the header is not set, the temporary user is added to the USERS built-in group.The repository connection opens.
The web application page is displayed, to which the user was redirected.
The use of external services is available only in the web application.
To set up authentication via external services, see the Setting Up Authentication via External Services section.
Guest Login
Guest login is available only in the web application and is recommended:
To get familiar with the web application. The user can log in without entering user credentials and using a previously created guest account.
On integration with IDM (Identity Management) systems to ensure asynchronous messaging via HTTP:
If access control in Foresight Analytics Platform is executed by an external centralized system.
When integrating with data bus (Enterprise Service Bus (ESB) class systems) when creating a highly loaded system architecture.
If guest login is used, it is recommended to limit guest account permissions. The web application should be started in an isolated environment.
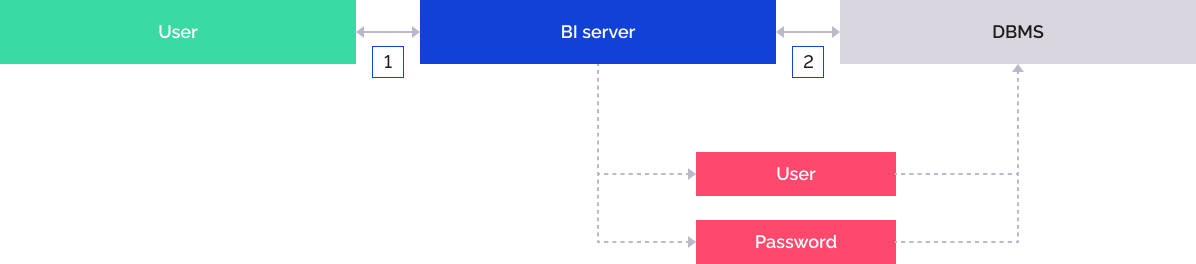
The user opens the guest link.
The BI server addresses DBMS by means of the previously entered guest account user name and password.
To use guest login, see the Setting Up Guest Login section.