Connecting Domain Group
Foresight Analytics Platform uses information from domain catalog service or global catalog for working with domain security subjects. A domain group can be connected if the following supported DBMS: PostgreSQL/Postgres Pro, Oracle, Microsoft SQL Server.
Domain groups can be added by the application administrator or the user included in the ADMINISTRATORS group. If roles are separated between the information security administrator and the application administrator, only the information security administrator has always the permissions to add domain groups. If it is required that another user can also add domain groups, he should be given additional privileges - Creating and Deleting Users and Changing User Permissions, Distributing Roles, Changing Policy.
For PostgreSQL/Postgres Pro DBMS it is required to prepare PostgreSQL server. Oracle-based DBMS require advanced settings, including a special mechanism of domain user authorization. If the repository is based on Microsoft SQL Server DBMS, a domain group of users can be connected only in the desktop application.
TIP. Before connecting domain groups it is recommended to check if LDAP settings are identical in the settings.xml files located in different environments. If the settings are identical, ensure correct work of domain groups by connecting them within the same application: either in the web application or in the desktop application.
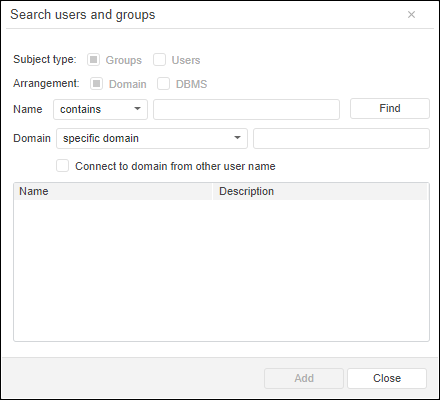
To connect a domain group of users in the Groups section:
After executing the operation a dialog box to select domain groups in the web applications and in the desktop application opens:
For details about how to work with dialogs of domain user group selection, go to the Selecting Users and Groups section.
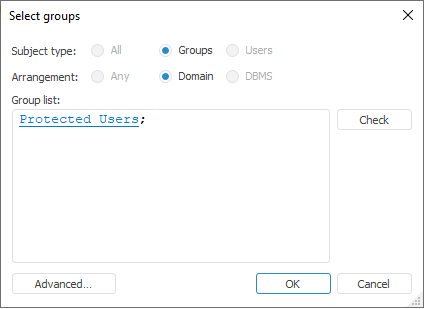
Select the required groups of users and click the OK button, after which the account creation dialog box opens:

When the Create on DB Server checkbox is selected, the group to be added is created on the database server, and the system requests credentials of the user, who has permissions to create users. This checkbox is deselected by default. If a domain group is connected in the repository based on PostgreSQL DBMS, the administrator should have the CREATEROLE privilege on the DBMS level.
When the Grant Rights on DBMS Level checkbox is selected, permissions for the added group are distributed at database level, and the system requests credentials of the user, who has permissions to create tables.
Select the Apply in All Similar Cases checkbox to perform the selected actions for all domain groups to repository to be updated without additional questions. This checkbox is selected by default.
Integrated Domain Authorization on Working with PostgreSQL DBMS Server
When integrated domain authentication is used that is specified in repository connection settings, the user can only log in via domain groups. Domain group permissions are applied to the DBMS users included in the group without explicit adding each account in the security manager.
To log in to the system via a domain group:
Make sure that domain group support is enabled in PostgreSQL DBMS. DBMS security subjects are synchronized with directory service subjects.
Connect a domain group in the security manager. In the Create Accounts dialog box select the Grant Permissions at DBMS Level checkbox.
Add privileges and set up access permissions for domain group objects.
After executing the operations the user included in the domain group can log in to the system.
Domain Authorization on Working with Oracle DBMS Server
A special mechanism of authorization of domain users who are not added in the security manager is implemented on working with the Oracle DBMS based repository. This mechanism uses domain groups with configured roles on the DBMS level. To enable the ability to add domain groups in the repository security manager, enable compatibility mode to work with domain groups in Oracle DBMS by means of the Fore language. After this the security manager will be able to connect domain groups.
To continue the setup, follow the steps:
Create a role on the DBMS server, give the CONNECT and RESOURCE grants for the role.
Add a domain user on the DBMS server. The adding method depends on DBMS settings and should correspond to the format used on repository connection. Include the user to the role created at Step 1.
In the security manager on the Groups tab add a domain group, in which the user is included. The group properties will have the Oracle DBMS Role box. The default role value is domain group name. In this box specify the role created at Step 1.
To add a domain group, grant required privileges or include the domain group to any existing group with configured access permissions - Administrators, Users, or other. If level based access control is used in the repository, determine the required access level for the domain group.
IMPORTANT. A unique role should be created for each domain group. It is not allowed to link different groups with the same role. It is not allowed to link several roles with the same domain group.
When the domain user who is not in the repository security manager is being connected, the system checks for the existence of this user in domain groups, which are connected in the security manager. If the user is included in any domain group, the system checks the correspondence of the role set for the group to roles created on the DBMS server. If the server contains the specified role, the user is connected. When level based access control is used, the user is connected according to the security level specified for the group. Otherwise the corresponding error message is displayed.
See also:
Creating Groups of Users and Working with Them | Creating and Editing Group of Users
 Group button on the toolbar.
Group button on the toolbar.