Setting Up Two-Factor Authentication
Two-factor authentication is intended to enhance information security using a user authentication verification on logon. As the first factor, any available authentication type is used. The second factor is a client certificate fingerprint saved in Foresight Analytics Platform.
The client certificate is a part of security certificate, which includes a set of generated certificates:
Root certificate. It is used to generate and sign server certificate and client certificate.
Server certificate. It is used by DBMS in the desktop application and web application server to sign client certificate.
Client certificate. It is a personal digital signature and it is used to verify its authentication during authorization.
By default, if user authentication is successful, the linked client certificate for system logon is requested.
To set up two-factor authentication:
Generate and install security certificate using specific crypto software, for example, OpenSSL.
NOTE. In the desktop application it is sufficient to link certificate to the user to use two-factor authentication with default settings, if standard configuration of Foresight Analytics Platform is used.
Set up web service connection, if one of configurations of Foresight Analytics Platform is used:
Standard configuration using the web application and the desktop application.
Standard configuration with web application use.
If required, change two-factor authentication application. By default, two-factor authentication is used for the users with a linked client certificate.
After executing the operations, the result of two-factor authentication depends on the specified application. If two-factor authorization application was not changed then linked client certificate will be requested for system logon if the user authentication is successful.
Linking a Client Certificate to User
The client certificate must be linked to each user individually.
To link certificate to user:
Execute one of the operations in the Users section:
In the web application select the user
In the desktop application:
Select a user and select the Properties context menu item.
Select a user and select the User > Properties main menu item.
Double-click the selected user.
After executing one of the operations the Properties side panel opens in the web application and the User Properties dialog box opens in the desktop application.
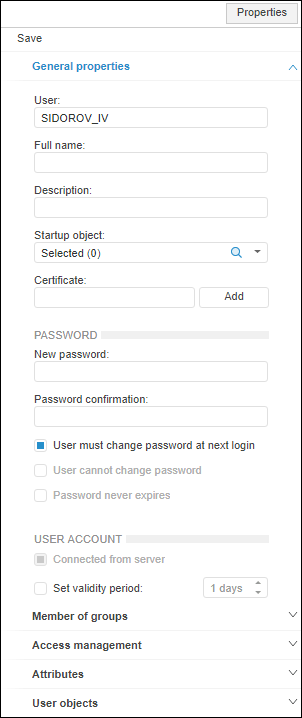
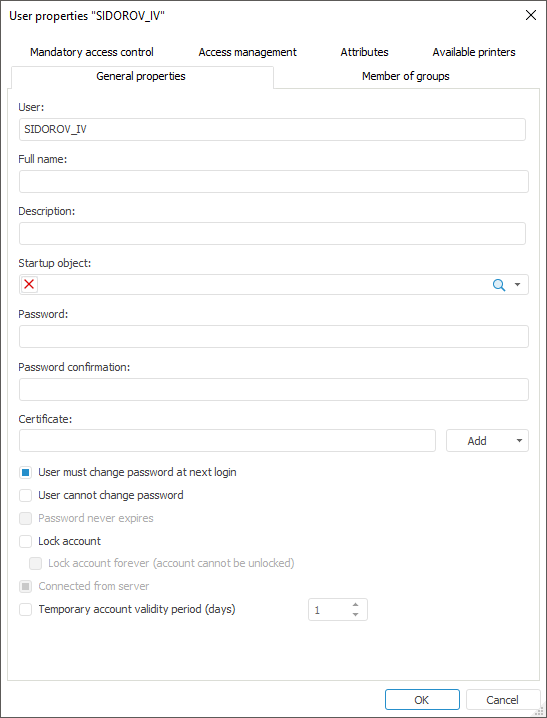
Click the Add button next to the Certificate box on the General Properties tab and select the client certificate option in the button's drop-down menu:
From file. A standard file selection dialog box opens. Select a file with *.cer or *.crt extension and click the Open button.
From Windows storage. A standard Windows certificate selection dialog box opens. Select a certificate and click the OK button.
NOTE. The web application only allows for adding a certificate from file.
After executing the operations, the Certificate box will contain a fingerprint of the selected client certificate.
Click the Save button in the web application or click the OK button in the desktop application.
After executing the operations, the client certificate will be linked to the selected user.
NOTE. In the desktop application it is sufficient to link a client certificate to the user to use two-factor authentication with default settings.
Setting Up Web Service Connection
Web service connection settings depend on operating system and configuration of Foresight Analytics Platform is used:
To set up web service connection in Windows OS:
Activate SSL parameters for the web application. Open a SSL settings setup page in the IIS service manager by clicking the
 SSL Settings button. After that the SSL Settings page opens. Select the Require SSL checkbox and the Require radio button for client certificates.
SSL Settings button. After that the SSL Settings page opens. Select the Require SSL checkbox and the Require radio button for client certificates.
To set up web service connection in Linux OS:
Apply settings in Linux OS:
For Debian-based distributions:
Enable the mod_ssl module for Apache2:
sudo a2enmod ssl
sudo a2ensite default-ssl
Create the /etc/apache2/ssl directory to store certificates and keys:
sudo mkdir /etc/apache2/ssl
Copy created certificate files and server certificate key: ca.cer, server.cer, server.key.
Set access permissions to the directory:
sudo chmod 0600 /etc/apache2/ssl
sudo chown -R www-data:www-data /etc/apache2/ssl
Set up web application server. The required web application settings are described in the Setting Up Apache2 to Access Web Application Resources on Astra Linux OS article. If SSL is used, some steps differ:
Add a variable for HTTPS protocol in the /etc/apache2/envvars file:
export PATH_TO_WEB=/opt/foresight/fp10.x-biserver
export PP_SOM_HTTPS=https://hostname.domain.ru/fpBI_App_v10.x/axis2/services/PP.SOM.Som
Edit /etc/apache2/sites-enabled/default-ssl file and add the following values to the <VirtualHost _default_:443> tag (by replacing hostname.domain.ru with server address):
ServerName hostname.domain.ru
Alias /fp10.x/app/ ${PATH_TO_WEB}/app/
Alias /fp10.x/build/ ${PATH_TO_WEB}/build/
Alias /fp10.x/dashboard/ ${PATH_TO_WEB}/dashboard/
Alias /fp10.x/resources/ ${PATH_TO_WEB}/resources/
Alias /fp10.x/index.html ${PATH_TO_WEB}/index.html
Alias /fp10.x/libs/ ${PATH_TO_WEB}/libs/
Alias /fp10.x/ ${PATH_TO_WEB}/
ProxyPass /fp10.x/app/PPService.axd ${PP_SOM_HTTPS} retry=1 acquire=3000 timeout=6000
Keepalive=On
SSLProxyEngine On
SSLProxyCheckPeerCN on
SSLProxyCheckPeerExpire on
ProxyPassReverse /fp10.x/app/PPService.axd ${PP_SOM_HTTPS}
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/server.cer
SSLCertificateKeyFile /etc/apache2/ssl/server.key
SSLVerifyClient require
SSLVerifyDepth 10
SSLCACertificateFile /etc/apache2/ssl/ca.cer
Restart Apache2 web server:
sudo service apache2 restart
For RedHat-based distribution files:
Enable the mod_ssl module for httpd:
sudo yum -y install mod_ssl
The configuration file /etc/httpd/conf.d/ssl.conf is created with module connection string:
LoadModule ssl_module modules/mod_ssl.so
NOTE. The 443 TCP port is opened for HTTPS connections, mod_ssl uses the openssl package, and support of the SSLv2 protocol is disabled by default.
Create the /etc/httpd/ssl directory to store certificates and keys:
sudo mkdir /etc/httpd/ssl
Copy created certificate files and server certificate key: ca.cer, server.cer, server.key.
Set access permissions to the directory:
sudo chmod 0600 /etc/httpd/ssl
sudo chown -R apache:apache /etc/httpd/ssl
Set up web application server:
Add a variable for the HTTPS protocol in the /etc/sysconfig/httpd file:
export PATH_TO_WEB=/opt/foresight/fp10.x-biserver
export PP_SOM_HTTPS=https://hostname.domain.ru/fpBI_App_v10.x/axis2/services/PP.SOM.Som
Edit the /etc/httpd/conf.d/ssl.conf file and add the following values to the <VirtualHost _default_:443> tag (by replacing hostname.domain.ru with server address):
ServerName hostname.domain.ru
Alias /fp10.x/app/ ${PATH_TO_WEB}/app/
Alias /fp10.x/build/ ${PATH_TO_WEB}/build/
Alias /fp10.x/dashboard/ ${PATH_TO_WEB}/dashboard/
Alias /fp10.x/resources/ ${PATH_TO_WEB}/resources/
Alias /fp10.x/index.html ${PATH_TO_WEB}/index.html
Alias /fp10.x/libs/ ${PATH_TO_WEB}/libs/
Alias /fp10.x/ ${PATH_TO_WEB}/
ProxyPass /fp10.x/app/PPService.axd ${PP_SOM_HTTPS} retry=1 acquire=3000 timeout=6000 Keepalive=On
SSLProxyEngine On
SSLProxyCheckPeerCN on
SSLProxyCheckPeerExpire on
ProxyPassReverse /fp10.x/app/PPService.axd ${PP_SOM_HTTPS}
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/server.cer
SSLCertificateKeyFile /etc/apache2/ssl/server.key
SSLVerifyClient require
SSLVerifyDepth 10
SSLCACertificateFile /etc/apache2/ssl/ca.cer
Restart httpd web server:
sudo service httpd restart
After executing the operations on two-factor authentication, the HTTPS protocol will be used for web service connection. User authorization will be executed by client certificates.
Changing Two-Factor Authentication Application
By default, two-factor authentication is used for the users with a linked client certificate.
Methods for changing application of two-factor authentication in the web application and in the desktop application differ.
In the web application create the Strategy_check string parameter and set its value in the settings.xml file:
<...>
<Key Name="Manager">
<Certificate Strategy_check="Always"/>
</Key>
</...>
Available parameter values:
User. Default. Two-factor authentication is used if the user has a linked client certificate.
Always. Two-factor authentication is used for all users. The users who do not have a linked client certificate are denied access.
Never. Two-factor authentication is not used if the user has a linked client certificate.
In the desktop application create the Strategy_check string parameter and set its value in the registry key HKEY_LOCAL_MACHINE\Software\Foresight\Foresight Analytics Platform\10.0\Manager\Certificate on local computers of all users.
Available parameter values:
User. Default. Two-factor authentication is used if the user has a linked client certificate.
Always. Two-factor authentication is used for all users. The users who do not have a linked client certificate are denied access.
Never. Two-factor authentication is not used if the user has a linked client certificate.