 User1. Restricted access (1).
User1. Restricted access (1).The mandatory access control method is used to grant permission via platform means and is based on assigning system objects and subjects with a security level. Object security levels determine access to stored information: the lower is the level, the higher is the security. Subject security levels determine access to information.
NOTE. The mandatory access control method can be used together with the discretionary access control method.
When the mandatory access control is used, all the information stored in the system is divided into categories. Each category can contain any number of security levels. The levels are comparable if they belong to the same information category. All security levels have different criticality labels. The lower is the label value, the higher is the security degree of the level.
Categories can be of two types:
Hierarchical. Hierarchical categories determine comparison relations between security levels by criticality label value. Thus, label comparison results in a higher or lower access level. If user criticality label is higher than the object label, the user gets read-only permission. If user criticality label is lower than the object label, the user gets write-only permission. If user and object criticality labels match, the user gets read and write permissions.
Non-Hierarchical. For a non-hierarchical category, criticality label comparison may result in label matching or mismatching, that is, scopes of security levels do not overlap. If the comparison results in label matching, the user gets read and write permissions. If the criticality labels do not match, access to object is denied.
The mandatory access control method is set up by:
The owner of the ADMIN schema.
Members of the Administrators group.
Users with the following privileges: Login; Changing User Permissions, Distributing Roles, Changing Policy; Changing Security Label and Access Control List of Any Object. Browsing all objects in the navigator; Read and Write Permission for All Objects.
Information security administrator on administrator roles separation.
To use mandatory access control method:
Select the Use Mandatory Access Control checkbox on the Access Control tab of the policies editor.
Create user accounts and groups of users.
Mandatory access control determines only the possibility to read and modify objects; permissions to delete objects are not determined by mandatory access control. In this context, editing objects means changing their contents or access permissions.
A subject can read an object:
For hierarchical categories: if user criticality label is lower or equal to object criticality label.
For non-hierarchical categories: only when user and object criticality labels match.
A subject gets write permissions:
For hierarchical categories: if user criticality label is higher or equal to object criticality label.
For non-hierarchical categories: only when user and object criticality labels match.
A subject gets read and write permissions if object and user criticality labels match.
When there are several information categories with different security levels, these rules must be satisfied for each category for the user to get permissions to read or edit the information.
The specific level with the security label 0 means that the user is denied to read and write information. A user with this level has no access to any repository object. If this level is assigned to an object, none of the users can have access to it.
Suppose, there are several security levels for a hierarchical category:
0. Access denied.
1. Restricted access.
2. Limited access.
3. Public access (general use).
And there are three users with the security levels:
 User1. Restricted access (1).
User1. Restricted access (1).
 User2. Limited access (2).
User2. Limited access (2).
 User3. Public access (3).
User3. Public access (3).
Therefore, the structure of the system can be shown as the chart:
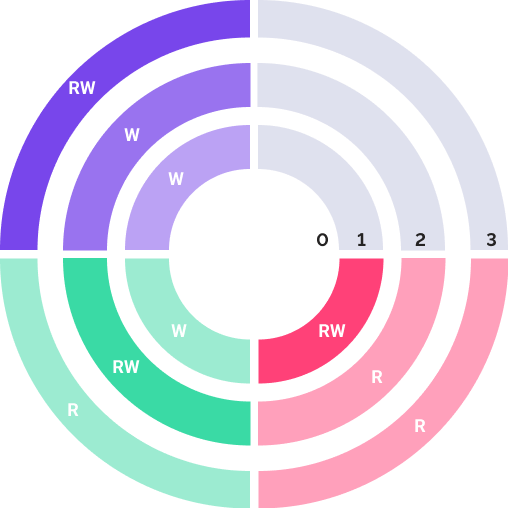
The circles represent security levels with corresponding criticality labels.
Labels:
RW. Read and write permissions.
R. Read permissions.
W. Write permissions.
Thus, in this system:
The User1 is allowed to:
Read and write objects with the Restricted Access (1) security level.
To read objects with the Limited Access (2) and Public Access (3) security levels.
The User2 is allowed to:
Read and write objects with the Limited Access (2) security level.
To read objects with the Public Access (3) security level.
To write objects with the Restricted Access (1) security level.
The User3 is allowed to:
Read and write objects with the Public Access (3) security level.
To write objects with the Limited Access (2) and Restricted Access (1) security levels.
All users cannot access objects with the 0 - Access Denied security level.
See also:
Selecting Access Control Methods and Their Setup | Adding Security Categories and Levels