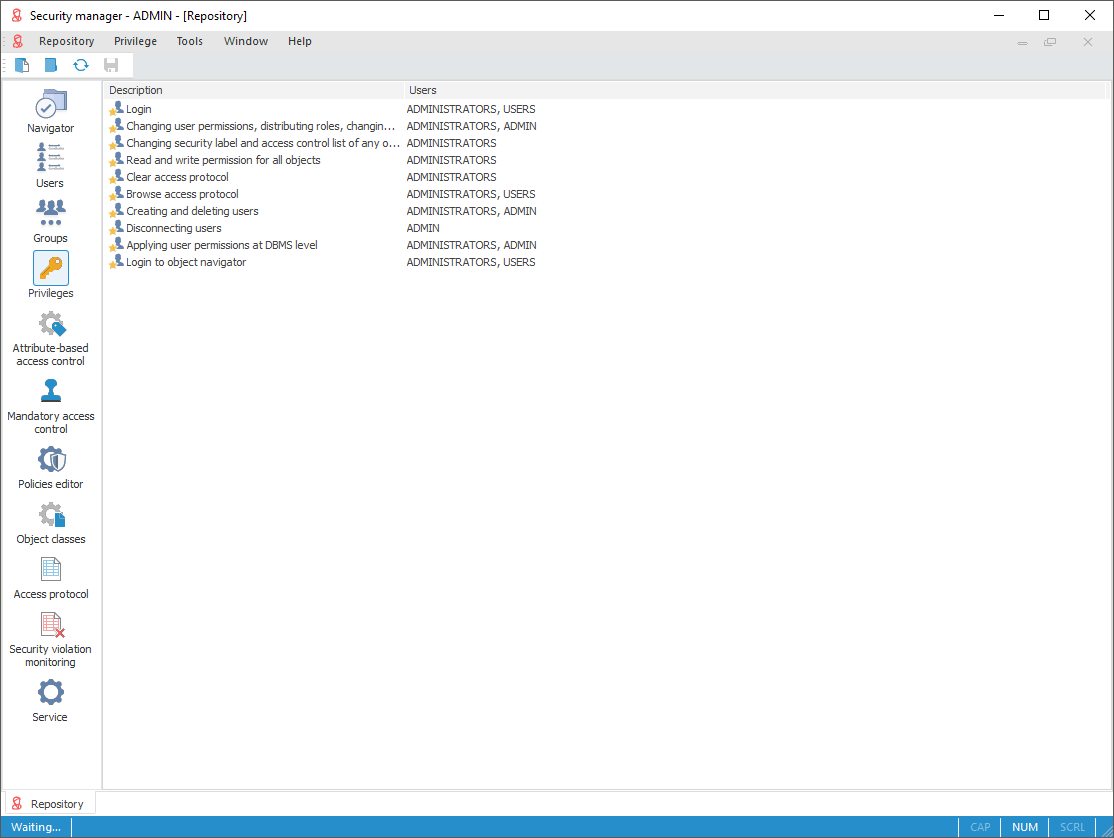
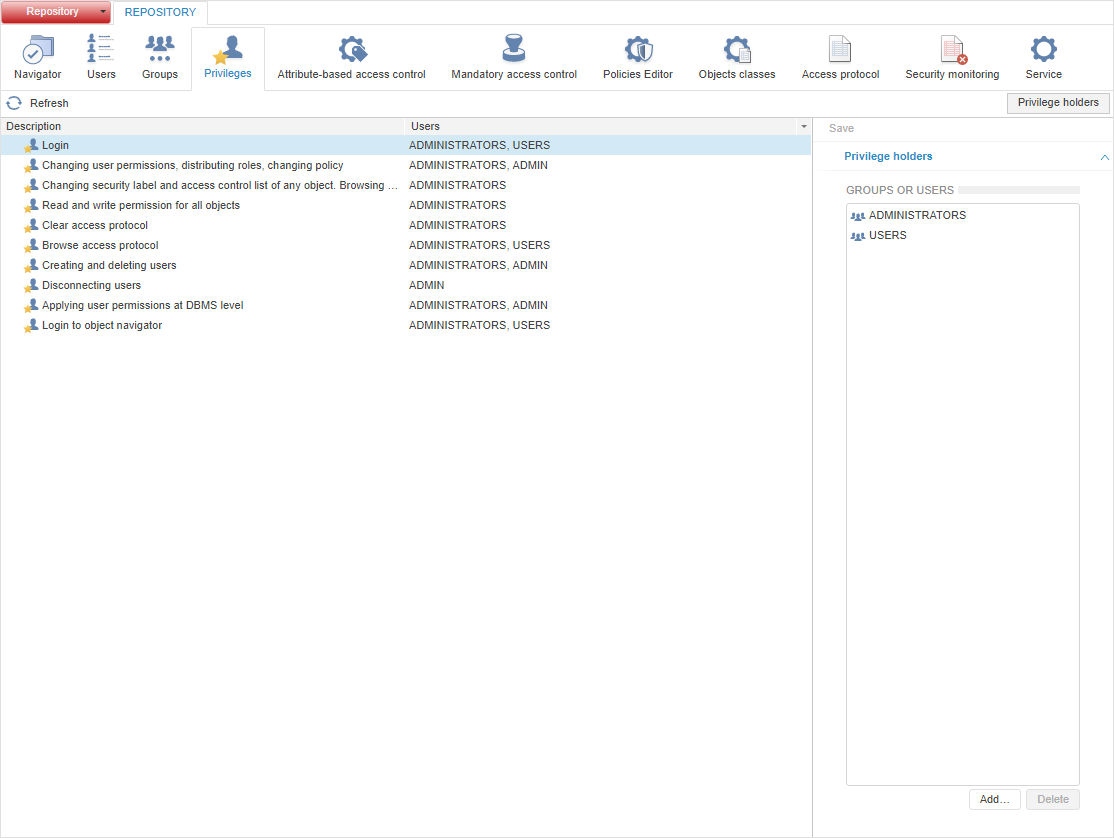
To distribute privileges between system users, use the Privileges section on the navigation panel.
NOTE. When roles of information security administrator and application administrator are separated, the Privileges section is available only for information security administrator.
The Privileges section:


There is a list of privilege holders next to each privilege.
Description of all system privileges:
| Privilege description | Possible operations | Privilege holders by default |
| Login | Login. | Administrators, users |
| Read and open all objects | Read permissions for all objects in the navigator. | Administrators |
| Changing security label and access control list of any object. Browse all objects in the navigator |
|
Administrators |
| Changing user permissions, distributing roles, changing policy |
|
Administrators |
| View access protocol | Viewing access protocol. | Administrators |
| Clear access protocol | Clearing access protocol. | Administrators |
| Creating and deleting users | Creating and deleting users. When a user is created, only the General Properties tab is displayed. | Administrators |
| Disconnecting users | Disconnecting users connected to the schema. | Administrators, *_ISA ( where * is SCHEMENAME) When roles of information security administrator and application administrator are separated, this privilege will be available only for ISA. |
| Applying user permissions at DBMS level | Updating users, updating groups of users. | Administrators |
| Login to object navigator | Open object navigator window. NOTE. The user who does not hold this privilege can open repository objects access permissions, for which he is granted. |
Administrators, users |
The Administrators group hold all privileges by default. The Users group has only the following privileges: Login and Login to Object Navigator.
Privileges are distributed by the administrator or the information security administrator.
To distribute privileges:
In the desktop application:
Select a privilege.
Open the Privilege Holders dialog box:
Select the Tools > Privilege Holders main menu item.
Select the Privilege Holders context menu item.
Double-click the privilege.
Performing one of these operations opens the Privilege Holders dialog box:
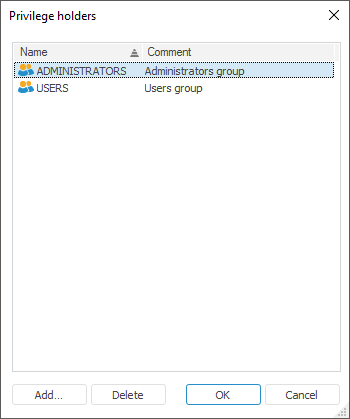
Click the Add button.
In the web application:
Select a privilege.
Click the Add button on the Privilege Holders side panel.
After executing the operations the Select Users and Groups or Search Users and Groups dialog box opens.
To delete the selected privilege holders, click the Delete button in the Privilege Holders dialog box in the desktop application and on the Privilege Holders side panel in the web application.
NOTE. If the domain user/group is selected as the privilege holder which is not created in Foresight Analytics Platform, the process of creating a domain user/domain group will be launched.
To apply the specified privilege settings:
In the desktop application:
Select the Repository > Apply Security Policy main menu item
Click the  Apply Security Policy button on toolbar
Apply Security Policy button on toolbar
In the web application:
Click the Save button on the side panel.
NOTE. If section parameters have been changed, an attempt to go to another section of the security manager or to close it displays a request to apply changed settings.
See also:
Setting Up System Security Policy | Setting Up Object Access Permissions | Setting Up User Action Auditing