In this article:
Setting Up Interaction of Client with Web Server via the HTTPS Protocol
Step 1. Place and Install Security Certificates
Setting Up Web Application to Work via HTTPS
Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP) that uses Transport Layer Security (TLS) protocol encryption. The TLS protocol is cryptographic and is used to create a secure communication channel between computers in network. Cryptographic methods ensure confidentiality and integrity of transmitted data, one-way or two-way authentication.
Security certificates are used to ensure trust between the server and client communicating via HTTPS protocol. Security certificates include a set of information about the certificate owner, the certificate owner's public key, the subject that issued and signed the certificate, and information for certificate validation.
The following types of security certificates are required to ensure communication between the server and the client via HTTPS protocol:
Root certificate. It belongs to Certification Authority (CA). Due to trust between the server and the client and the root certificate, a chain of trust is built for the rest of the certificates. Therefore, a common space of trust is created.
Intermediate certificate. It belongs to an intermediate certification authority and is signed by the root certification authority or another intermediate certification authority. Hierarchy of certification authorities is used to solve various frequent tasks for issuance and service of issued certificates.
Server certificate. It is used for authentication of the Apache2 web server in Linux OS or IIS in Windows OS.
Foresight Analytics Platform also supports web application work via HTTPS protocol with the use of GOST encryption. The GOST encryption requires the use of cryptographic information protection tools (CIPT): CryptoPro CSP, ViPNet CSP, Crypto-COM, MagPro CryptoPacket, and others. CIPT must be compatible with operating environment of Foresight Analytics Platform and must be installed both on web application server and client device. CIPT are not included in Foresight Analytics Platform setup software package. Web application work via HTTPS protocol using the GOST encryption is set up in accordance with the documentation for the corresponding CIPT.
For details about web application work in the Chromium-Gost browser using CryptoPro CSP, see to the Setting Up Web Application to Work in Chromium-Gost Browser section.
Set up one of the options of interaction between web application configuration elements:
Client > HTTPS > web server > HTTPS > BI server.
Client > HTTPS > web server > HTTP > BI server.
When working in the web application via the HTTPS protocol additionally set up web forms, to work via the WebSocket protocol. For details see the Setting Up Web Forms via HTTPS section.
Setting Up Interaction of Client with Web Server and Web Server with BI Server via the HTTPS Protocol
Consider setting up interaction of client with web server and web server with BI server via the HTTPS protocol in Linux OS. Web server and BI server can be located on one physical server or one different ones.
To set up interaction of client with web server and web server with BI server via the HTTPS protocol:
Make sure that there are the following directories in the system:
For BI server:
/opt/foresight/fp10.x-biserver. Main files of BI server.
/etc/apache2-fp10.x. Configuration files of Apache2 instance with BI server for Debian-based distributions.
/etc/httpd-fp10.x. Configuration files of Apache2 instance with BI server for RedHat-based distributions.
/etc/httpd2-fp10.x. Configuration files of Apache2 instance with BI server for ALT Linux.
For web server:
/opt/foresight/fp10.x-webserver. Main files of web server.
/etc/opt/foresight/fp10.x-webserver. The additional configuration file envvars of web server instance to set Apache2 environment variables.
/etc/apache2-fp10.x-web. Configuration files of Apache2 instance with web server for Debian-based distributions.
/etc/httpd-fp10.x-web. Configuration files of Apache2 instance with web server for RedHat-based distributions.
/etc/httpd2-fp10.x-web. Configuration files of Apache2 instance with web server for ALT Linux.
NOTE. The specified directories are created by default during web application setup.
Determine DNS name of server:
sudo hostnamectl set-hostname <DNS name of server>
Download and unpack the enable_https.zip archive. Place the enable_https.sh script in the /home/<user name> home directory.
Open the enable_https.sh script for edit and change values of preconfigured parameters if the system contains a set of ready security certificates:
CERT_DIR=./fp-certs
SERVER_CRT_NAME="fp_server.crt"
SERVER_KEY_NAME="fp_server.key"
Description of variables:
CERT_DIR. The path to the folder with security certificates. Default path: ./fp-certs.
SERVER_CRT_NAME. Name of server certificate file with the *.crt extension. Default name: fp_server.crt.
SERVER_KEY_NAME. Name of private key name of server certificate with the *.key extension. Default name: fp_server.key.
NOTE. Skip the step to generate automatic self-signed security certificates. Self-signed certificates are linked to the DNS name of server determined at the Step 2.
Change the current directory to the folder with the script:
cd /home/<user name>/enable_https.sh
Grant access permissions for script execution:
sudo chmod +x enable_https.sh
Run the script:
If URL of the PPService.axd: web server is specified in web application configuration files.
sudo ./enable_https.sh
If URL of the PP.SOM.Som web server is specified in configuration files:
sudo ./enable_https.sh service
If web server and BI server are located at different physical servers, DNS name of BI server and web server are requested on script execution.
After executing the operations the web application is set up to work via the HTTPS protocol. If designer of business applications back end was set up using the DBA.war archive before web application work setup via the HTTPS protocol, designer of business applications work will also be set up via the HTTPS protocol.
During script execution:
The HTTP protocol is changed to HTTPS in web application configuration files:
/opt/foresight/fp10.x-webserver/r/config/config.json;
/opt/foresight/fp10.x-webserver/config/PP.xml;
The <VirtualHost *:8810> section is added with SSL and CORS settings for BI server:
/etc/apache2-fp10.x/mods-available/fp10.x-biserver.conf in Debian-based distributions.
/etc/httpd-fp10.x/conf.d/fp10.x-biserver.conf in RedHat-based distributions.
/etc/httpd2-fp10.x/conf/mods-enabled/fp10.x-biserver.conf in ALT Linux.
SSL settings and paths to security certificates are added for web server:
/etc/apache2-fp10.x-web/sites-available/webserver.conf in Debian-based distributions.
/etc/httpd-fp10.x-web/conf.d/00-virtualhost.conf in RedHat-based distributions.
/etc/httpd2-fp10.x-web/conf/sites-enabled/000-default.conf in ALT Linux.
The PP_SOM variable is changed in the /etc/opt/foresight/fp10.x-webserver/envvars file.
The /home/<user name>/fp-certs folder is created with self-signed security certificates if the Step 4 was skipped: the fp_server.crt server certificate the fp_server.key private key of server certificate; the fp_ca.crt root certificate; the fp_ca.key private key of root certificate. Self-signed certificates are valid during 1024 days.
Server certificate and its private key are copied from the folder specified in the CERT_DIR variable to the /opt/foresight/ssl/ folder.
Files with the *.bak extension are added to save backup of changed files. Each file is created in the folder with changed file. For example, the file /opt/foresight/fp10.x-webserver/r/config/config.json.bak containing settings for running the script.
Setting Up Interaction of Client with Web Server via the HTTPS Protocol
Consider setting up interaction of client with web server via the HTTPS protocol. In this case the web server and BI server will communicate via HTTP protocol. It is assumed that the web server and BI server are located on the same physical server.
Step 1. Place and Install Security Certificates
NOTE. Before executing the step see the certification authority service provider guide and the operating system documentation.
To place and install security certificates:
Generate and save the server.key private key of the certificate.
Create a request to get the domain_name.csr server certificate.
Get the server.cer server certificate for Linux OS or the server.pfx server certificate for Windows OS signed by the certification authority that is trusted by all system users.
Get the ca.cer root certificate and subca.cer intermediate certificates if they are in the trust chain.
Place the certificates and keys for installation:
On the user's local computer - the ca.cer root certificate file.
On the server - the server.cer server certificate file, the server.key server certificate private key file for the Apache2 server in Linux OS or server.pfx for IIS web server in Windows OS.
TIP. It is recommended to include certificates of intermediate certification authorities to the server certificate file and exclude the root certificate from the server certificate. If required, change the server certificate file in a text editor.
The specified certificate and key files are given as an example and may differ.
Step 2. Import Root Certificate to Store
To import a root certificate to the trusted root certification authority store, use the supported browser or operating system tools. Operating system tools can be used to import certificate to store only in Windows OS.
Consider certificate import in Mozilla Firefox:
Open browser settings at:
about:preferences
Open the Privacy and Security section.
Click the View Certificates button in the Certificates subsection. The Certificate Manager dialog box opens.
Click the Import button on the Authorities tab. A standard file selection dialog box opens.
Select the ca.cer root certificate. The Load Certificate dialog box opens.
Select the trust This CA to Identify Websites checkbox.
After executing the operations the root certificate is imported to the trusted root certification authority store.
To import the root certificate to a trusted root certification authority store using Windows OS tools:
Double-click the ca.cer root certificate. The Certificate dialog box opens.
Click the Install Certificate button. The certificate import wizard opens.
Select the Current User store location and click the Next button.
Select the Place All Certificates to the Following Store radio button, select the Trusted Root Certification Authorities certificate store in the Select Certificate Store dialog box and click the Next button.
After executing the operations the root certificate is imported to the trusted root certification authority store.
For other options of certificate installation and import in various operating systems and browsers see the public services portal.
Step 3. Set Up Web Server
Setup steps differ depending on the web server and operating system in use.
To set up Apache2 web server in Linux OS:
Connect the mod_ssl module:
Debian-based distributions:
sudo a2enmod-fp10.x-web ssl
sudo a2ensite-fp10.x-web default-ssl
RedHat-based distributions:
sudo yum install -y mod_ssl
sudo cp /etc/httpd/conf.modules.d/00-ssl.conf /etc/httpd-fp10.x-web/conf.modules.d/
sudo systemctl restart httpd-fp10.x-web
ALT Linux:
sudo apt-get install -y apache2-mod_ssl
sudo cp /etc/httpd2/conf/mods-available/ssl.load /etc/httpd2-fp10.x-web/conf/mods-available/
sudo /usr/sbin/a2enmod-fp10.x-web ssl
sudo systemctl condreload httpd2-fp10.x-web.service
After executing the operations the mod_ssl module is connected. For details about the module see the Apache2 documentation.
In RedHat-based distributions the /etc/httpd-fp10.x-web/conf.d/ssl.conf configuration file is created with the module connection string:
LoadModule ssl_module modules/mod_ssl.so
In ALT Linux the /etc/httpd2-fp10.x-web/conf/mods-enabled/ssl.load configuration file is created with the module connection string:
LoadModule ssl_module /usr/lib64/apache2/modules/mod_ssl.so
Add SSL parameters to the <VirtualHost> section in the web server configuration file:
/etc/apache2-fp10.x-web/sites-available/webserver.conf in Debian-based distributions.
/etc/httpd-fp10.x-web/conf.d/00-virtualhost.conf in RedHat-based distributions.
/etc/httpd2-fp10.x-web/conf/sites-enabled/000-default.conf in ALT Linux.
SSLEngine On
SSLCertificateFile <path to folder>/server.cer
SSLCertificateKeyFile <path to folder>/server.key
SSLProxyEngine On
In the <path to folder> substitution specify the folder with the server certificate and its private key.
NOTE. Add additional TLS protocol parameters generated using the SSL Configuration Generator tool.
Change HTTP protocol to HTTPS in the web application configuration files /opt/foresight/fp10.x-webserver/r/config/config.json, /opt/foresight/fp10.x-webserver/config/PP.xml and make sure that the following conditions are satisfied:
The config.json file contains URL of the PPService.axd web service in the serviceUrl field.
The PP.xml file contains the <proxy> section.
The example of the config.json file:
{
"targetRepo": "",
"serviceUrl": "https://<DNS name of server>:8110/fp10.x/app/PPService.axd",
"locale": "ru",
"locales": ["ru"],
"title": "FAP10",
"baseUrl": "https://<DNS name of server>:8110/fp10.x/",
"themes": ["fap10"]
}
The example of the PP.xml file:
<?xml version="1.0" encoding="utf-8"?>
<pp>
<proxy url="" />
<metabase id="WAREHOUSE" />
<serviceCM ParamsUrl="https://<DNS name of server>:8110/fp10.x/r/#/settings"/>
<modules commonModulesUrl="https://<DNS name of server>:8110/fp10.x/r/#">
</modules>
</pp>
Restart the web server:
Debian-based distributions:
sudo systemctl restart apache2-fp10.x-web
RedHat-based distributions:
sudo systemctl restart httpd-fp10.x-web
ALT Linux:
sudo systemctl restart httpd2-fp10.x-web
After executing the operations the Apache2 web server is set up.
To set up IIS web server in Windows OS, open the home page of the IIS manager and execute the operations:
Open the Server Certificates feature in the IIS section by double-click or using the Open Feature context menu item.
Select the Import item on the Actions panel. The Import Certificate dialog box opens:
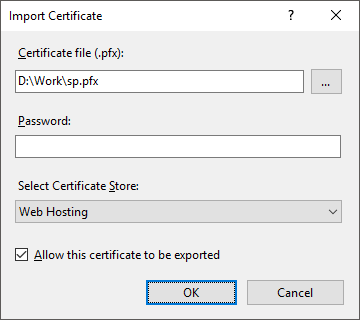
Set the parameters:
Certificate File (.pfx). Specify path to the server certificate server.pfx.
Password. Specify the password that was used on server certificate creation.
Select Certificate Store. Select the Web Hosting option in the drop-down list.
Click the OK button.
Select the site in the Sites list and select the Bindings item on the Actions panel. The Site Bindings dialog box opens.
Click the Add button. The Add Site Binding dialog box opens:
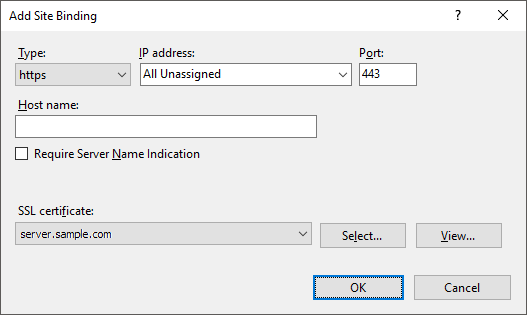
Set the parameters:
Type. Select the https option in the drop-down list.
SSL Certificate. Select the server corresponding to the imported server certificate in the drop-down list.
Add TLS protocol parameters to the registry using the IIS Crypto utility.
Change the HTTP protocol to HTTPS and make sure that DNS name of server is specified in the web application configuration files PP.xml, config.json.
Select the server in the Connections list and select the Restart item on the Actions panel.
After executing the operations the IIS web server is set up.
Step 4. Open Web Application via HTTPS Protocol
To open the web application via HTTPS protocol, use the supported browser and specify URL in the connection string:
In Linux OS:
https://<DNS name of server>:8110/fp10.x/r/
In Windows OS:
https://<DNS name of server>/FP_App_v10.x/r/