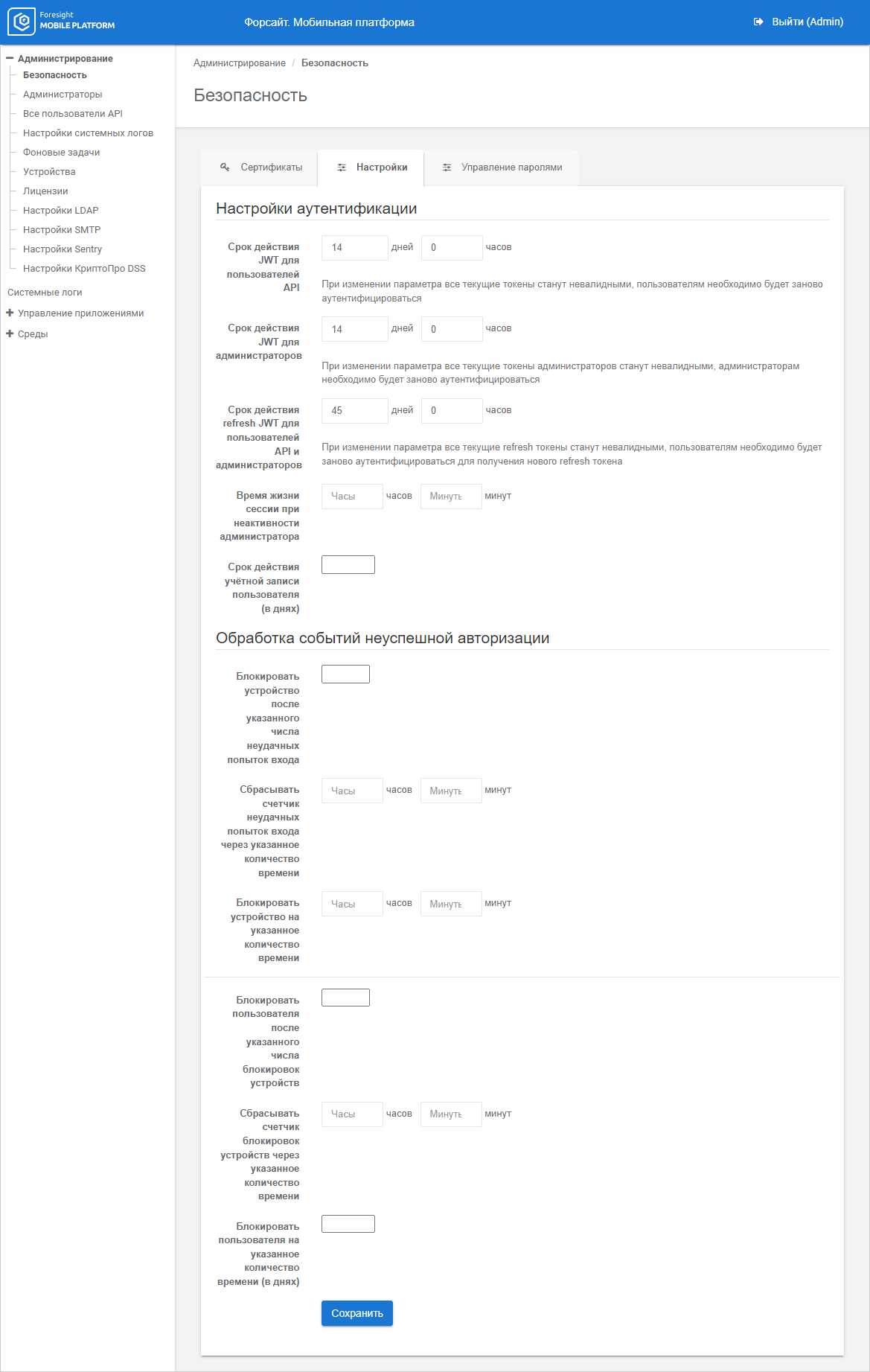
To set up security parameters, go to the Settings tab in the Security subsection:

When authentication is executed on a mobile platform server, the JWT token of the API user or administrator is created. JWT token is an object that is passed in request when a subject addresses mobile platform server API for authorization. Refresh JWT is an object that is required for refreshing JWT token.
To increase transfer security of the data that identifies a subject, a digital signature is applied to JWT token with the use of private encryption key. If required, the private encryption key can be changed. For details see the Changing Private Encryption Key of JWT Token section.
To change JWT token expiration time for subjects, specify the number of days, hours and minutes next to the JWT Token Expiration Time for API Users, JWT Token Expiration Time for Administrators parameters. The default JWT token expiration time is 14 days.
To change refresh JWT expiration time for subjects, specify the number of fays and hours next to the Expiration Time of refresh JWT for API Users and Administrators parameter. The refresh JWT is valid through 45 days by default.
NOTE. The refresh JWT expiration time should be greater than the JWT token expiration time for API users and administrators. When the JWT token or refresh JWT expiration time is changed, all the current tokens are invalid, it is required to repeat authentication for subjects.
To change the private key used on creating access and refresh JWT tokens of subjects, click the Generate button next to the Generate JWT Signature for API Users and Administrators parameter. After executing the operation it is asked to confirm generation of a new private key. If the answer is positive, the private key is changed. The private key is changed on demand, for example, if private key should be updated for security reasons.
IMPORTANT. If the private key changes, the current access and refresh JWT tokens of subjects will be invalid. The users and administrators should again execute authentication in the administrator console and on mobile devices.
To set session lifetime when the administrator is inactive, specify expiration time as follows: <hours : minutes> next to the Session Lifetime when Administrator is Inactive parameter. On an attempt to execute an operation in the administrator console after the specified time expires, the administrator should repeat authentication to continue working in the administrator console. The session lifetime is not set by default.
To set expiration time for all accounts of API users, specify the number of days in the User Account Expiration Time (in days) box. By default, validity is not set, accounts are not limited in time.
To set validity for a specific API user, use the Account Validity box in API user parameters. If validity is set for a specific API user, the specified user account validity is ignored in authentication settings.
To handle API user failures, determine the parameters:
Lock device after the specified number of failed logins.
Reset counter of failed logins in the specified time.
Lock device during the specified time.
Lock user after the specified number of device locks.
Reset counter of device locks in the specified time.
Lock user during the specified time (days).
If the specified number of authorization failures for the specific time period is exceeded, the mobile device is locked for the specified period. When the mobile device is locked, API user cannot be authorized on this device. If the number of mobile device locks for the specific time period is exceeded, API user is locked for the specified period. When the specified parameters of authorization failure handling are changed for locked API users, locking time is recalculated.
When API user is locked, the Locked for Security Reasons checkbox is automatically selected, and the message "Locked until <Date>" is displayed in specific API user parameters. When API user is locked, authorization is disabled, user session is interrupted on all mobile devices.
To unlock API user, deselect the Locked for Security Reasons checkbox or wait until the end of the specified user lock period.
See also: