Access control methods are determined by security policy. The security policy contains parameters that have global effect on the system security level. A security level for specific object can be determined by changing access control and criticality labels.
Permission and privilege owners are security subjects — users and groups of users.
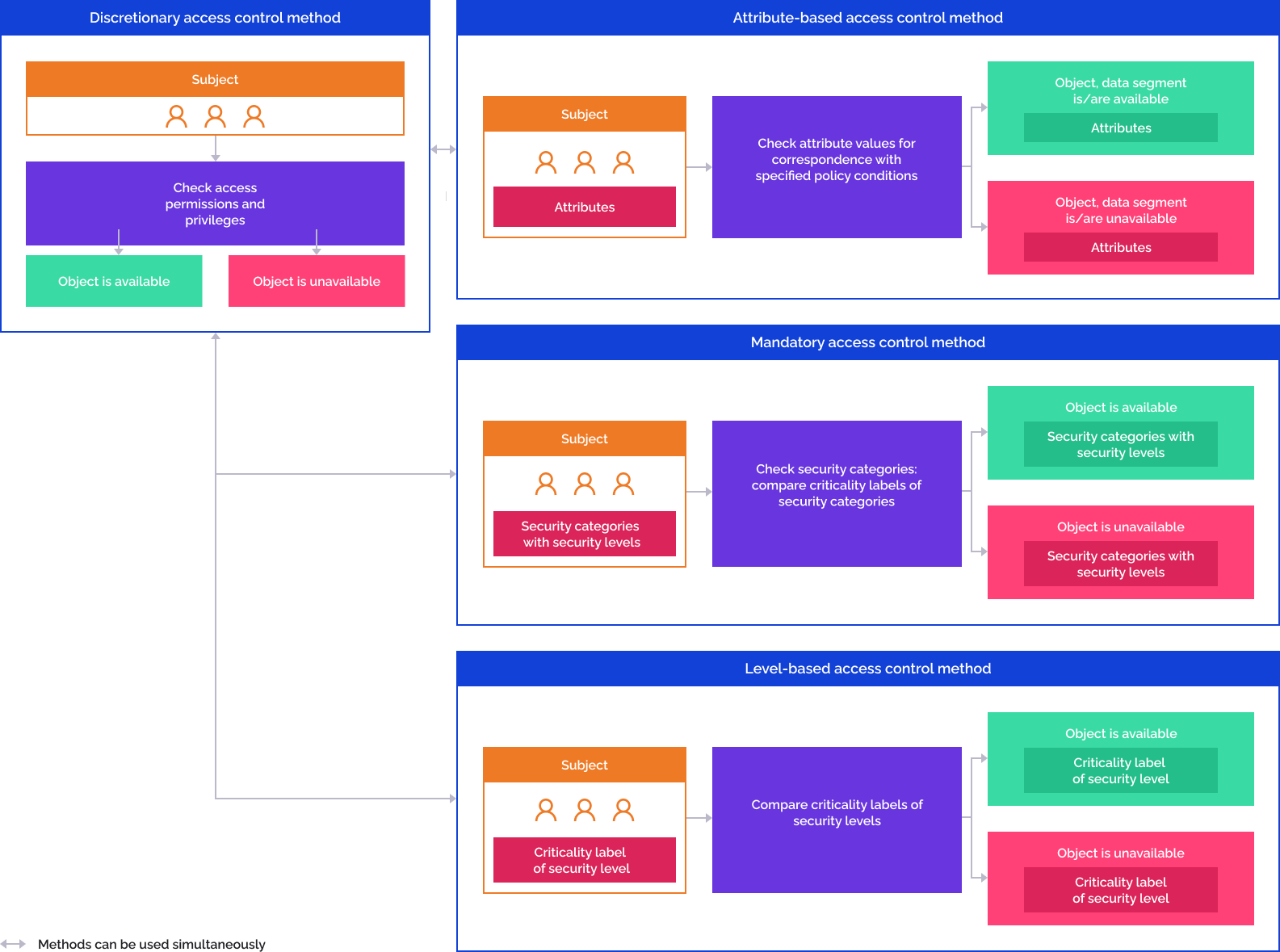
The security manager supports complementary access control methods:

Control over user actions in the system means checking if the user has a privilege necessary to execute these operations. Control of users accessing objects and executing various operations with them is executed by checking for the presence of permissions necessary to execute specific operations with objects.
Discretionary access control method grants permissions on DBMS level. Mandatory access control, level-based access control method and attribute-based access control method grant permissions on platform level. Attribute-based access control method is a data filtering when user accesses data via rules and policies check.
To get detailed information about access control methods, see the Setting Discretionary Access Control Method, Setting Mandatory Access Control Method, Setting Up Level-Based Access Control Method, Setting Up Attribute-Based Access Control Method sections.
If required, use role separation between information security administrator (ISA) and application administrator (AA). By default role separation is not used, and all functions are executed by system administrator.
To set up general security policy, see the General Policy Settings article.
To set up advanced access control, see the Advanced Access Control Settings article.
To set up access control for workstations and printers, see the Setting Up Access Control for Workstations and Printers article.
To set up user password check, see the Setting Up User Password Check article.
To manage access control methods, use the Access Control tab in the Policies Editor section of the navigation panel.
NOTE. When roles of information security administrator and application administrator are separated, the Policies Editor section is available only for information security administrator.
The Access Control tab:
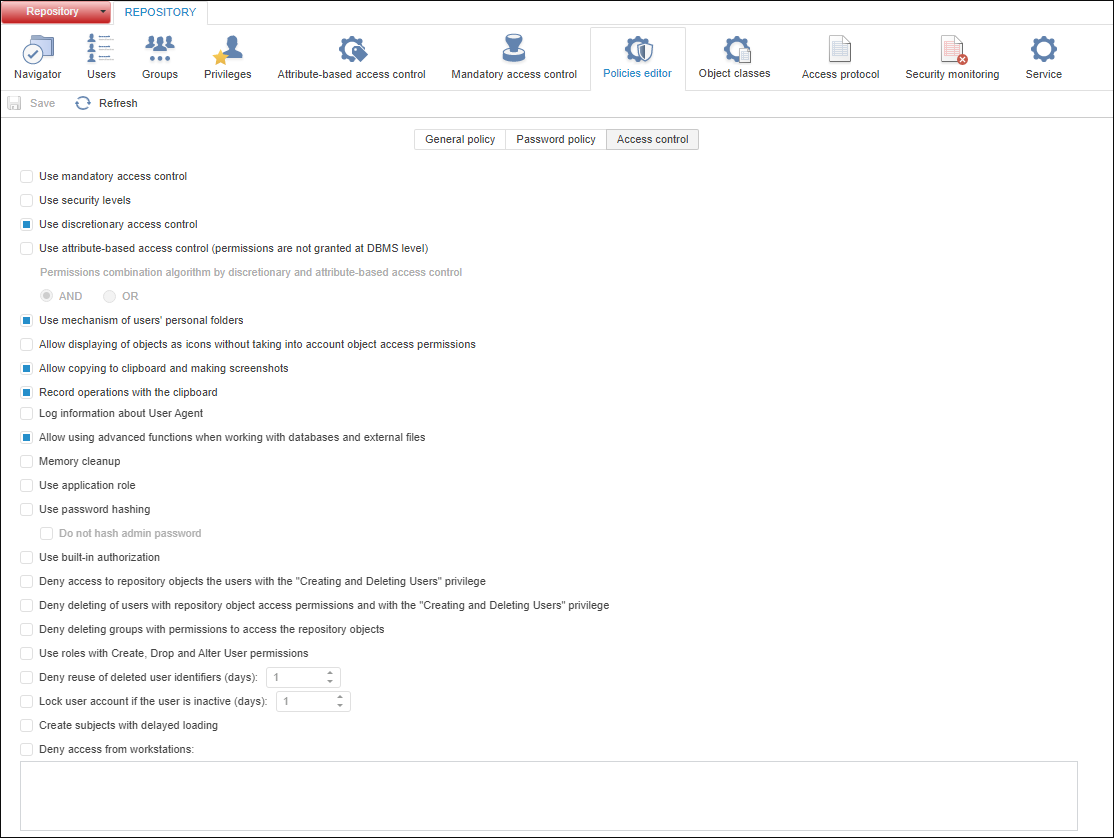
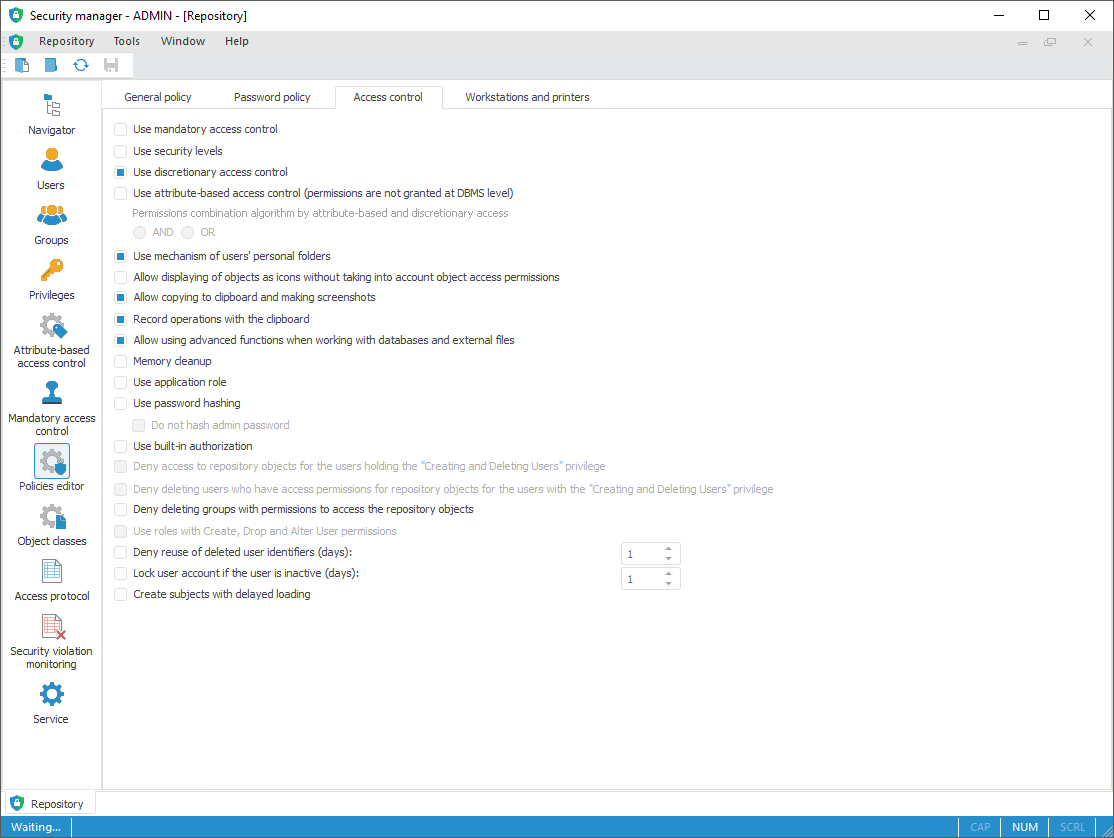
Select access control methods:
To use discretionary access control method, select the Use Discretionary Access Control checkbox.
To use mandatory access control method, select the Use Mandatory Access Control checkbox.
To use level-based access control method, select the Use Security Levels checkbox.
To use attribute-based access control method, select the Use Attribute-Based Access Control checkbox. On using attribute-based and discretionary access control methods, select the permission combination algorithm:
AND. The operation is allowed if the operation is allowed simultaneously for two access control methods. If the operation is denied for one of access control methods or access permissions are undefined, the operation is denied.
OR. The operation is allowed if operation permission is set up for at least one of access control methods, and access permissions are undefined for the other access control method. If the operation is denied for one of access control methods, the operation is denied.
NOTE. The discretionary access control is set in the access control by default.
To apply the specified access control settings:
In the web application click the  Save button on the toolbar or on the side panel.
Save button on the toolbar or on the side panel.
NOTE. If section parameters have been changed, an attempt to go to another section of the security manager or to close it displays a request to apply changed settings.
See also:
Setting Up System Security Policy | Creating User Accounts and Working with Them | Creating Groups of Users and Working with Them