Select the object.
Click the
 Dependent Objects button on the toolbar.
Dependent Objects button on the toolbar.
Dependent object permission setup enables the user to set up permissions to all objects used by this object or use this object.
To set up dependent object access permissions:
In the web application:
Select the object.
Click the  Dependent Objects button on the toolbar.
Dependent Objects button on the toolbar.
After executing the operations the Discretionary Access Control and Mandatory Access Control tabs are displayed for the selected object.
In the desktop application:
Select the object.
Select the Set Up Dependent Object Permissions checkbox on the Discretionary Access Control or Mandatory Access Control tab in the Access Control Settings dialog box.
Click the OK button.
After executing the operations the Set Up Dependent Object Permissions dialog box opens.
NOTE. Displaying of the Mandatory Access Control tab in the desktop application and the ability to set mandatory access control permissions in the web application depend on the configured security policy.
The Discretionary Access Control tab, when setting up dependent object permissions, is available in the web application and in the Set Up Dependent Object Access Permissions dialog box in the desktop application:
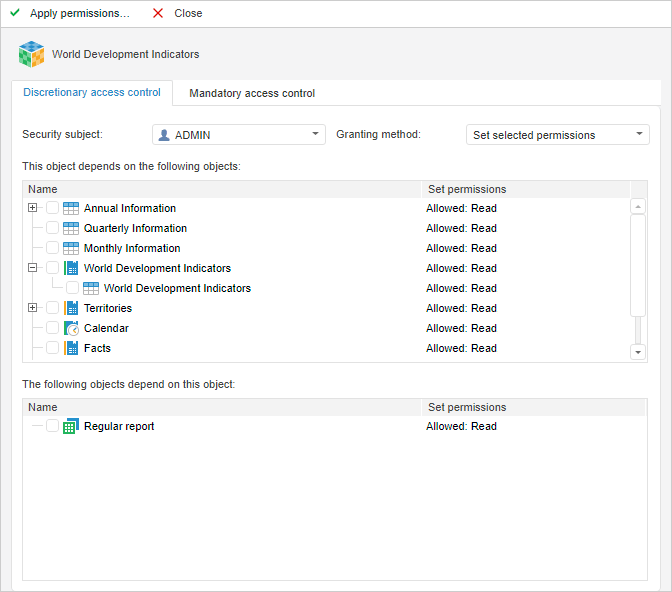
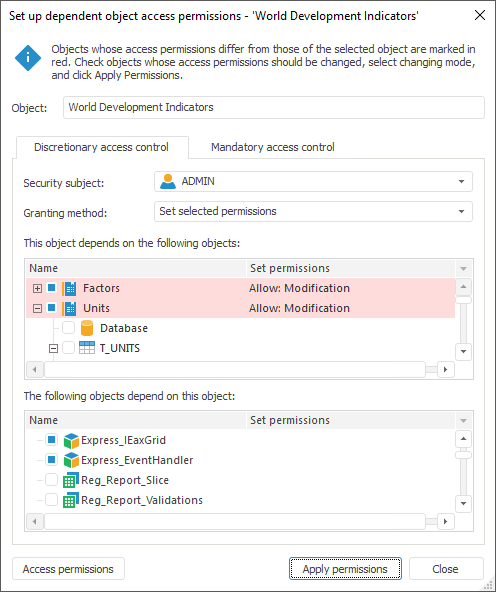
The access permission setup contains:
Object. The box displays name of the source object, for which dependent objects are considered.
Security Subject. In the drop-down list select the security subject for which it is required to set up access permission for dependent objects.
Granting Method. In the drop-down list select the methods of access permissions application to dependent objects:
Set Selected Permissions. Permissions of the selected objects will be replaced with the permissions of the source.
Add Selected Permissions. Permissions of the source object will be added to permissions of the selected objects.
This Object Depends on the Following Objects. All dependent objects are displayed in the list (by descending hierarchy).
The Following Objects Depend On This Object. All dependent objects are displayed in the list (by ascending hierarchy)
Apply Permissions. The column displays object permissions Unmatched with the initial object permissions.
Select checkboxes of the objects, permissions for which need to be changed.
NOTE. Those objects which permissions do not match the permissions of the source object are to be marked in red. For those objects checkboxes are selected automatically.
The Mandatory Access Control tab, when setting up dependent object permissions, is available in the web application and in the Set Up Dependent Object Access Permissions dialog box in the desktop application:
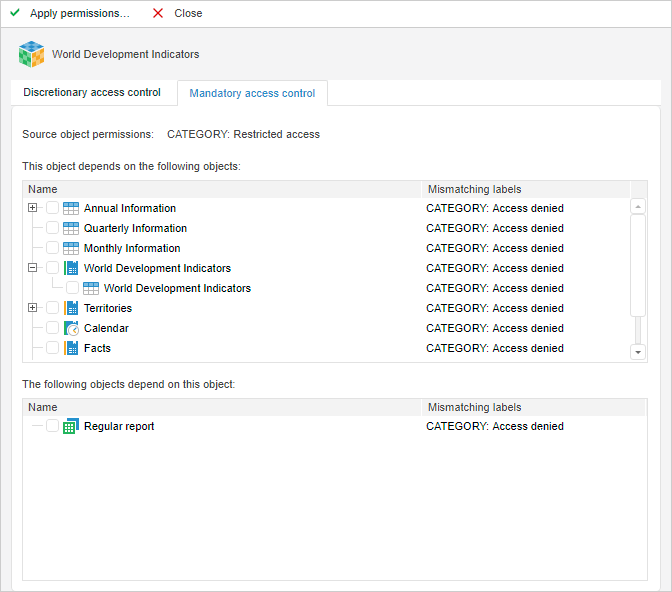
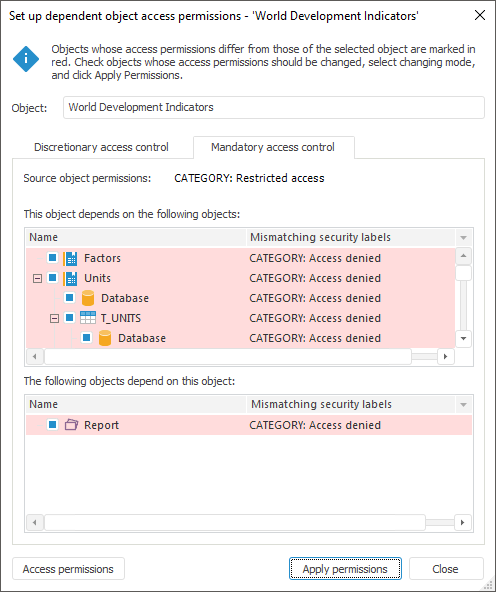
The access permission setup contains:
Source Object Permissions. The field contains security labels of all the security categories for the initial object. When the mouse cursor is pointed to this box, a tooltip appears if all the categories do not fit into the available space.
This Object Depends on the Following Objects. All dependent objects are displayed in the list (by descending hierarchy)
The Following Objects Depend On This Object. All dependent objects are displayed in the list (by ascending hierarchy).
Unmatched Security Labels. The column displays object security labels matching with source object labels in the format: <category name>: <level name>.
Select checkboxes of the objects, security labels of which should match the initial object labels.
NOTE. Those objects which permissions do not match the permissions of the source object are to be marked in red. For those objects checkboxes are selected automatically.
To view and change access permissions for the selected object:
In the web application use the Discretionary Access Control/Mandatory Access Control tab on the Properties side panel.
In the desktop application click the Access Permissions button in the Set Up Dependent Object Access Permissions dialog box. The Access Control Settings dialog box opens.
To apply permissions for the selected objects, click the Apply Permissions button. After this the action confirmation dialog box opens. If the answer is positive, object permissions will be changed taking into account the method for granting source object permissions in discretionary or mandatory access control.
When closing the Set Up Dependent Object Access Permissions dialog box in the desktop application or when moving to another section in the web application, the system requests to apply permissions for the selected objects.
See also: