In this article:
Step 1. Import Client Certificate to Store
Step 2. Link Client Certificate to User
Setting Up Two-Factor Authentication
Two-factor authentication is used to enhance information security due to additional user verification during authorization. The selected authentication type is used as the first factor. The second factor is a client certificate fingerprint saved in Foresight Analytics Platform.
The client certificate is a part of the security certificate, which includes several generated certificates:
Root certificate. It is used to generate and sign server certificate and client certificate.
Server certificate. It is used by the Apache2 server in Linux OS or by IIS in Windows OS ion the web application.
Client certificate. It is used to verify the user during authorization and is a personal digital signature.
By default, if user authentication is successful, the linked client certificate for system logon is requested.
NOTE. Two-factor authentication setup is available in the desktop application and in the web application, which is set up to work via HTTPS protocol. To ensure two-factor authentication work, web application configuration files must contain URL of the PP.SOM.Som web service.
If two-factor authentication is set up for the web application, it is assumed that the root certificate and server certificate have been already generated and installed during web application work setup via HTTPS protocol. Generate only the client.pfx client certificate and place it in the folder with the root certificate on the user's local computer. Generate the client certificate with the *.cer or *.crt extension to assign it to the user in Foresight Analytics Platform.
If two-factor authentication is set up for the desktop application, generate the root certificate and the client certificate signed by the trusted certification authority. Next, create a folder and place the certificates on the user's local computer: the client.pfx client certificate, the ca.cer root certificate, and the ca.key private key.
The specified certificate and key files are given as an example and may differ.
Step 1. Import Client Certificate to Store
To import client certificate to a personal certificate store, use supported browser or operating system tools. Operating system tools can be used to import certificates to stores only in Windows OS.
Consider certificate import in Mozilla Firefox:
Open browser settings at:
about:preferences
Open the Privacy and Security section.
Click the View Certificates button in the Certificates subsection. The Certificate Manager dialog box opens.
Click the Import button and execute the operations. A standard file selection dialog box opens.
Select the client.pfx client certificate on the Your Certificates tab.
Enter the private key password that was specified on client certificate creation.
After executing the operations the client certificate is imported to personal certificate store.
Step 2. Link Client Certificate to User
The client certificate must be linked to each user individually.
NOTE. Linking client certificate to domain user is unavailable.
To link a certificate to the user in the security manager:
Execute one of the operations in the Users section:
In the web application select the user.
In the desktop application:
Select the user and select the Properties context menu item.
Select the user and select the main menu item: User > Properties.
Double-click the selected user.
After executing one of the operations the Properties side panel opens in the web application and the User Properties dialog box opens in the desktop application.
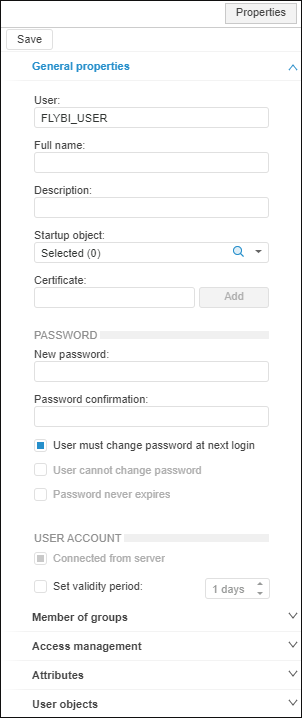
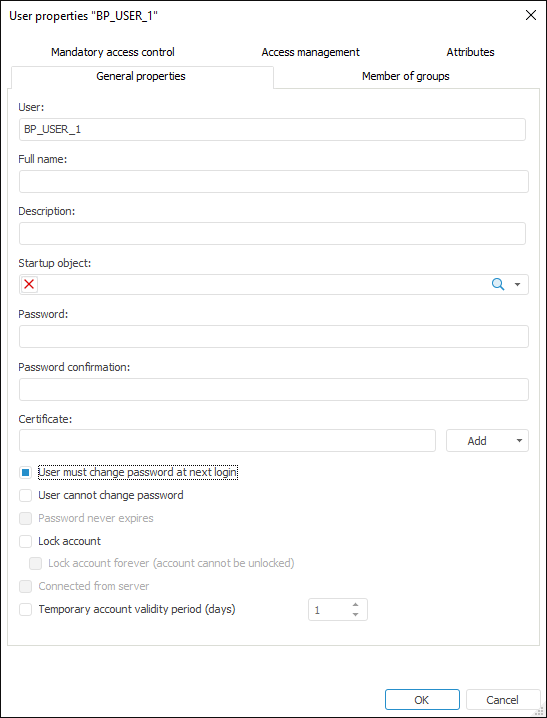
Click the Add button next to the Certificate box on the General Properties tab and select the client certificate add option in the button's drop-down menu:
From File. A standard file selection dialog box opens. Select a file with the *.cer or *.crt extension and click the Open button.
From Windows Storage. A standard Windows certificate selection dialog box opens. Select a certificate and click the OK button.
NOTE. The web application only allows for adding a certificate from file.
After executing the operations, the Certificate box contains a fingerprint of the selected client certificate.
Click the Save button in the web application or click the OK button in the desktop application.
After executing the operations the client certificate is linked to the selected user.
Step 3. Setting Up BI Server
Steps for BI server installation differ depending on the operating system in use.
To set up BI server in Linux OS:
Add SSL parameters to the configuration file:
/etc/apache2-fp10.x/mods-available/fp10.x-biserver.conf in Debian-based distributions.
/etc/httpd-fp10.x/conf.d/fp10.x-biserver.conf in RedHat-based distributions.
/etc/httpd2-fp10.x/conf/mods-available/fp10.x-biserver.conf in ALT Linux.
<VirtualHost *:8810>
...
SSLVerifyClient require
SSLVerifyDepth 10
SSLCACertificateFile <path to folder>/ca.cer
...
</VirtualHost>
In the <path to folder> substitution specify the folder with the root certificate.
After executing the operations the BI server is set up.
To set up IIS web server, on which BI server is installed in Windows OS, open the IIS manager and execute the operations:
Open the
 SSL Settings feature in the IIS section by double-click or using the Open Feature context menu item.
SSL Settings feature in the IIS section by double-click or using the Open Feature context menu item.Select the Require SSL checkbox and the Require radio button for client certificates.
After executing the operations on two-factor authentication, the HTTPS protocol will be used for web service connection. User authorization will be executed by client certificates.
Step 4. Change Two-Factor Authentication Application
By default, two-factor authentication is used only for the users with a linked client certificate. If required, change two-factor authentication application.
Methods for changing two-factor authentication application in the web application and in the desktop application differ.
In the web application create the Strategy_check string parameter and set its value in the settings.xml configuration file:
<Key Name="Manager">
<Certificate Strategy_check="Always"/>
</Key>
Available parameter values:
User. Default value. Two-factor authentication is used if the user has a linked client certificate.
Always. Two-factor authentication is used for all users. The users who do not have a linked client certificate are denied access.
Never. Two-factor authentication is not used even if the user has a linked client certificate.
In the desktop application create the Strategy_check string parameter and set its value in the registry key [HKEY_LOCAL_MACHINE\Software\Foresight\Foresight Analytics Platform\10.0\Manager\Certificate] on local computers of all users.
Available parameter values:
User. Default value. Two-factor authentication is used if the user has a linked client certificate.
Always. Two-factor authentication is used for all users. The users who do not have a linked client certificate are denied access.
Never. Two-factor authentication is not used even if the user has a linked client certificate.
Step 5. Check Two-Factor Authentication
To check two-factor authentication:
Open the web application via HTTPS protocol or start the desktop application.
Log in to the system with the used authentication type.
After executing the operations, the result of two-factor authentication depends on the specified application. If two-factor authorization application was not changed, linked client certificate will be requested for system logon if the user authentication is successful.