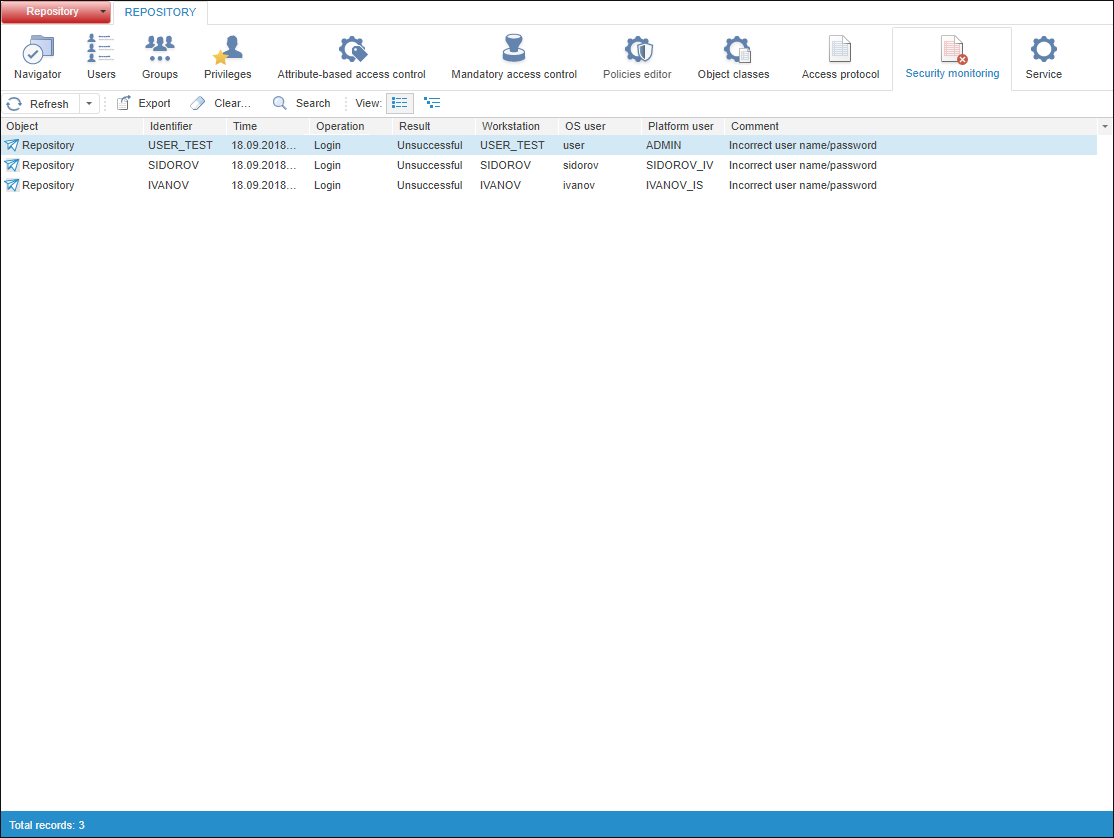
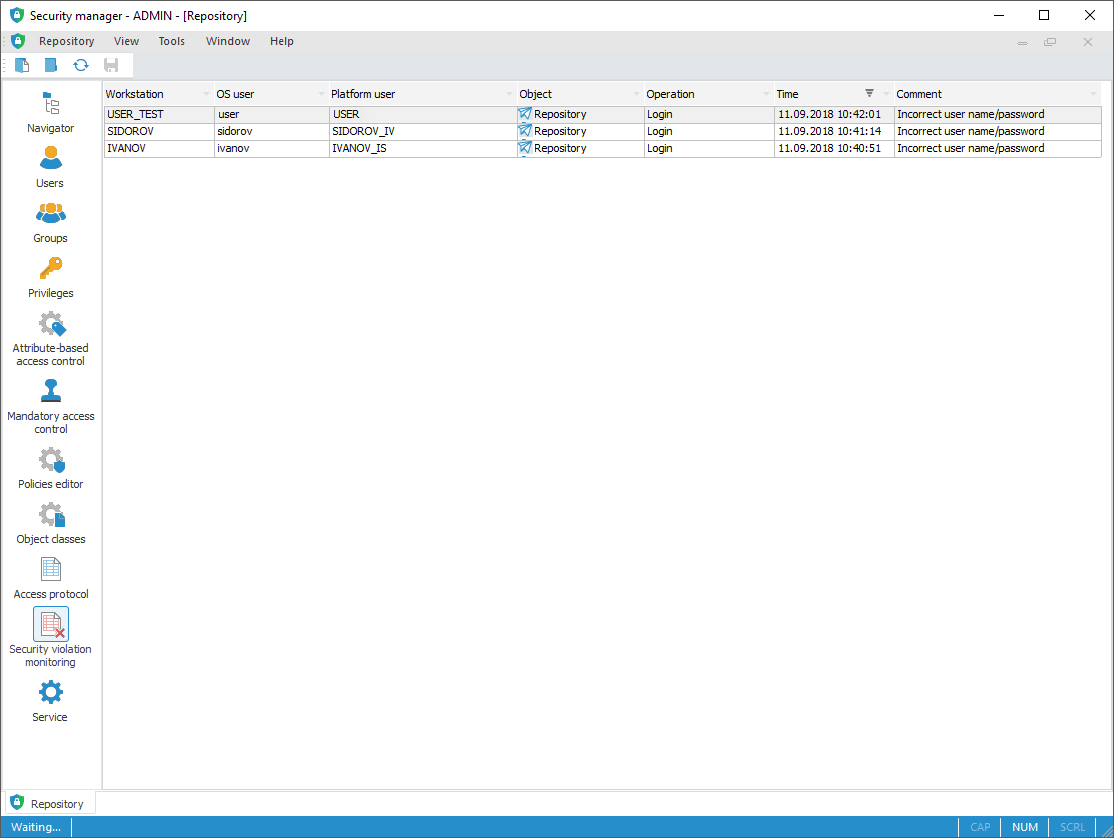
To monitor security violations, use the Security Violation Monitoring section on the navigation panel.
NOTE. When roles of information security administrator and application administrator are separated, the Security Violation Monitoring section is available only for information security administrator.
The Security Violation Monitoring section:


As a result of the lack of access permissions, the current attempts to violate the system security are recorded: failed login attempts and actions on the objects.
NOTE. In the desktop application, security violations are registered only if the Security Violation Monitoring section is opened. When the security manager is closed, security violation records are not saved.
 Search for security violation records
Search for security violation records
 Clear security violation monitoring
Clear security violation monitoring
For details about providing centralized monitoring of information security events see the Support of Work with Security Information and Event Management Systems article.
See also:
Tracking System Security Violations | Access Protocol | Controlling Foresight Analytics Platform and Metadata Integrity