To add access check rules and policies, use the Attribute-Based Access Control section on the navigation panel.
NOTE. When roles of information security administrator and application administrator are separated, the Attribute-Based Access Control tab is available only for information security administrator. Attribute-base access control structure creation (attribute addition, policy and rules editing) is controlled by the system and it is available to administrator with Changing User Permissions, Distributing Roles, Changing Policy or Change Security Mark and List of Control Access of Any Object privileges.
The section is based on the attribute-based access control method, it is used to create access check rules with necessary conditions. The system checks whether a user can execute a specific action on an object and/or data segment through an attribute check.
NOTE. The attribute-based access control method can be used simultaneously with the discretionary access control method.
Attributes are divided into system and custom, they are used on creating an objective and additional conditions of access control. System attributes are read-only, only custom attributes can be added or edited for users, groups of users, object classes, particular object types, particular objects depending on the defined task.
NOTE. Custom attributes are added before getting started with the section.
Make sure that the Use Attribute-Based Access Control checkbox is used in the access control.
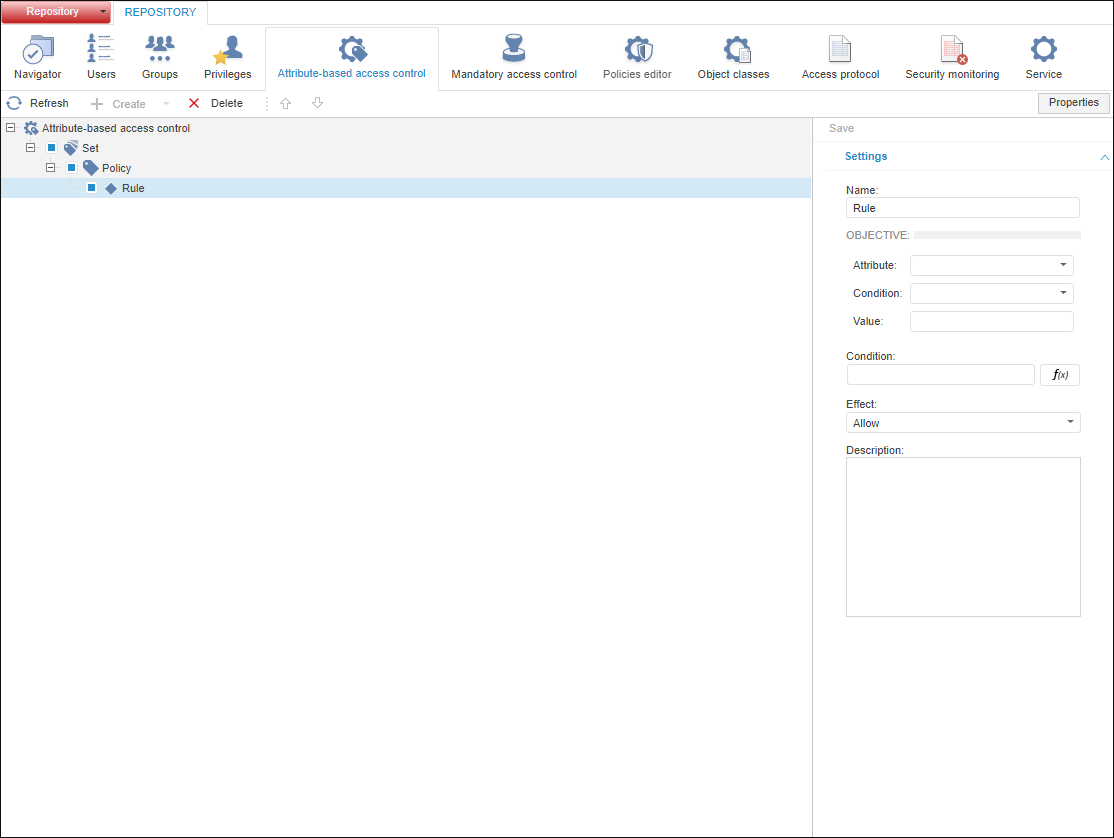
The Attribute-Based Access Control:


The section contains a structure of attribute-based access control that consists in the elements hierarchy:
Attribute-Based Access Control is at the first level, the structure of policies sets, policies and rules is determined here.
Policies sets are at the second level.
Policies are at the third level.
Rules are at the fourth level.
IMPORTANT. If attribute-based access control structure is not specified, all operations with objects are denied.
Key features:
 Determine attribute-based access control properties
Determine attribute-based access control properties
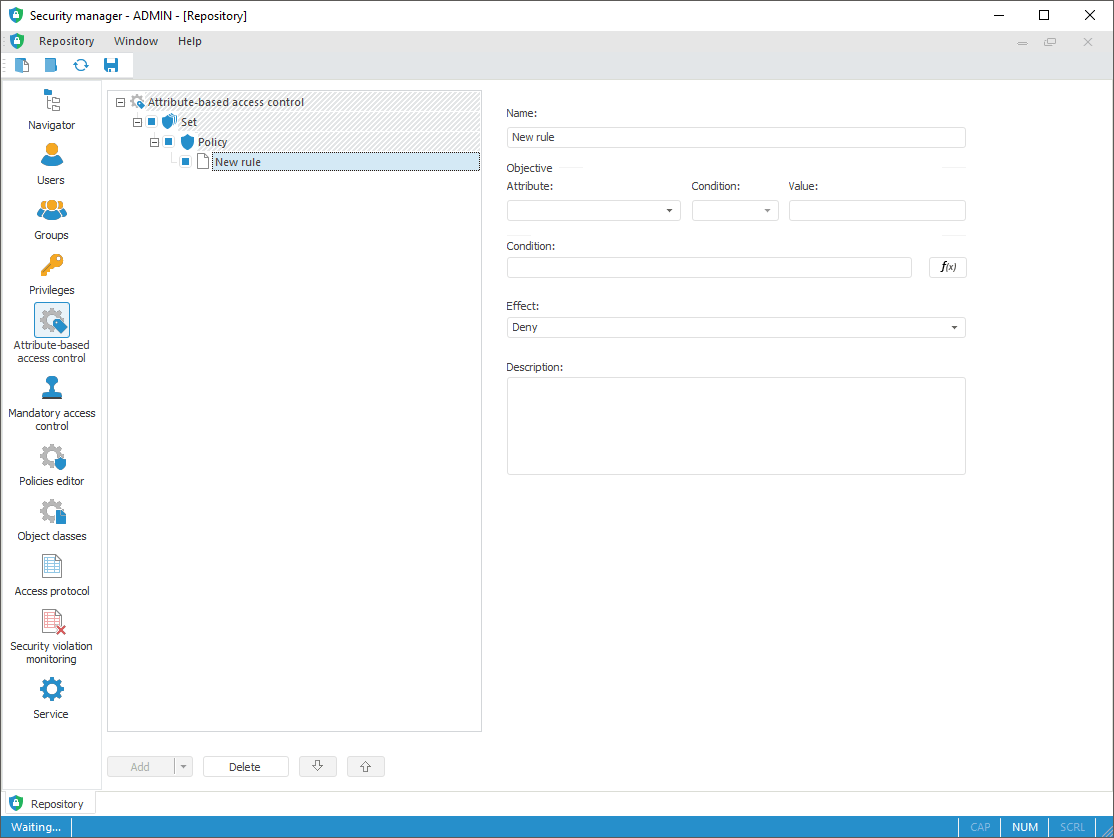
To create an access check policy:
Make sure that the required attributes are added for users, groups of users, object classes, particular types of objects, particular objects.
Add a policies set that unites policies and policies sets in one condition.
Add a policy containing access check conditions.
Add a rule containing additional conditions of the access control.
Set properties determining access to objects.
Determine structure of access control using checkboxes next to attribute-base access control elements.
Save the specified policy of the access control:
In the web application click the Save button on the side panel.
In the desktop application click the  Save button on the toolbar.
Save button on the toolbar.
After creating an access check policy the section will display attribute-based access structure.
To optimally place attribute-based access control elements in the structure, use the  Up and
Up and  Down buttons or Drag&Drop mechanism.
Down buttons or Drag&Drop mechanism.
If required, delete the attribute-based access control elements using the Delete button.
See also:
Setting Up Attribute-Based Access Control Method | Creating Custom Attributes