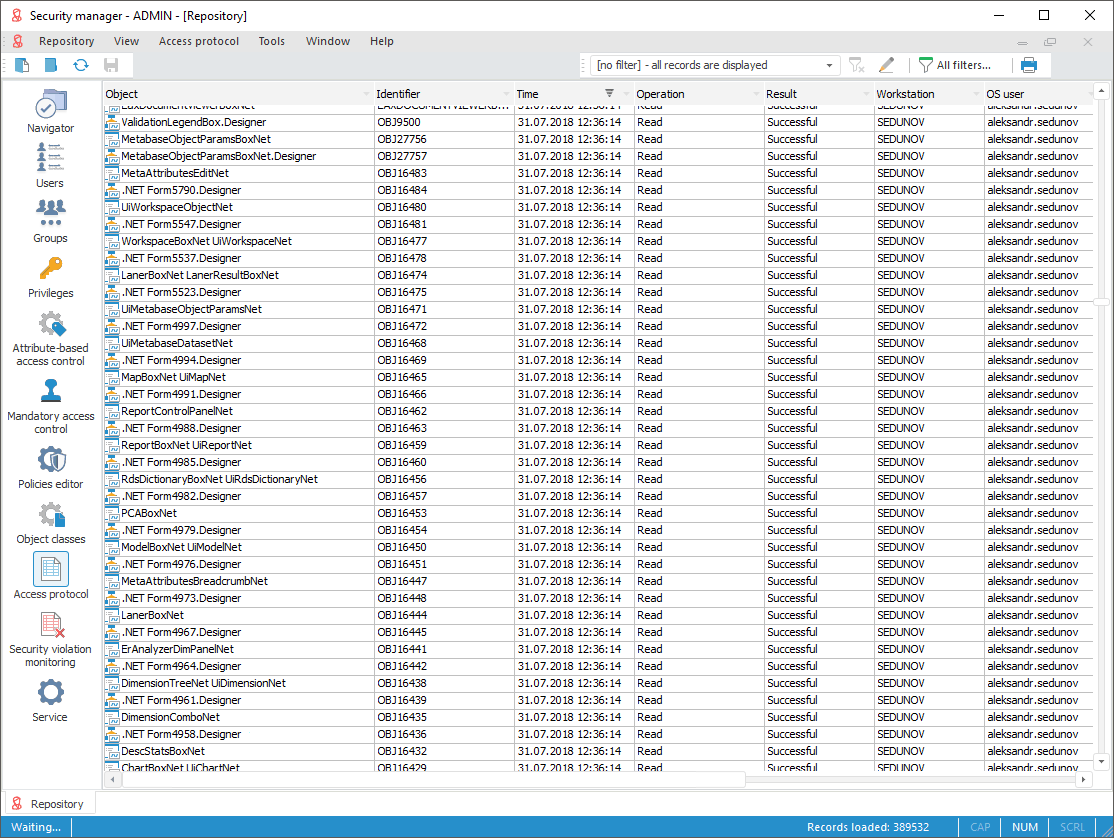
To track system security violations, use the Access Protocol and Security Violation Monitoring sections.
The security manager automatically audits subject actions in the system and records action information into the access protocol.
To get detailed information about the access protocol, see the Access Protocol section.

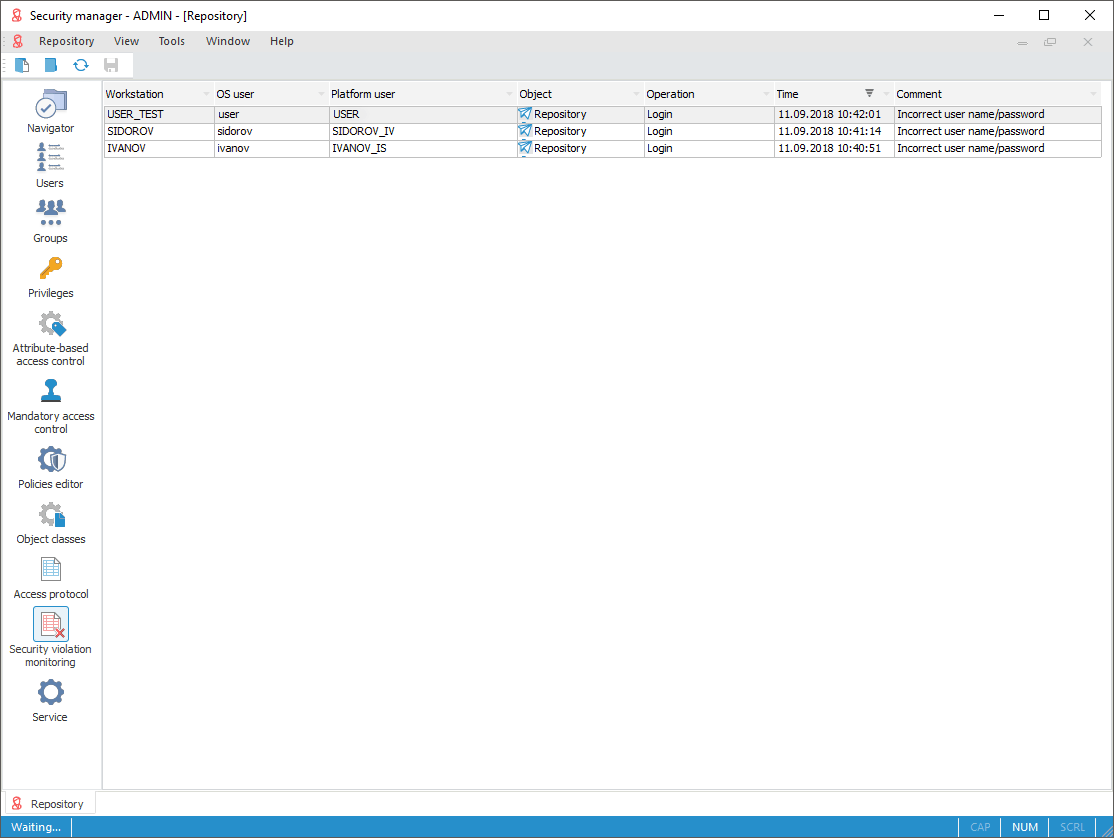
The security manager checks user access permissions and registers system violations on failed system logins and unavailable object actions.
To get detailed information about security violation monitoring, see the Security Violation Monitoring section.
See also: