Attribute-based Access Control method grants permissions on analytics platform level, it is a data filtering when a user accesses data by checking policies and rules. Method of attribute-based access control ( Attribute-based access control, ABAC) is implemented via access control model, which is aimed to optimize access control subsystem. Attribute-based access control is considered as a separate type of access control as discretionary and mandatory ones.
NOTE. The attribute-based access control method can be used simultaneously with the discretionary access control method. The combination algorithm of two methods is defined in the access control.
The access is restricted via policies and rules that contains a set of conditions to check attributes. This method provides the possibility to create combinations of conditions for expressing various policies. Granting user access to the object or data segment occurs only if the values of the user and object attributes allow the user to grant the access to the object.
Attribute-based method is determined by the elements:
Set of policies. It consolidates policies or sets of policies, determines whether an action or access to an object/data segment is possible based on policies.
Policy. It consolidates a set of rules and determines whether an action or access to an object/data segment is possible based on policies.
Rules. It determines the possibility to execute an action or access an object/data segment.
Attributes. Attributes of subjects and objects/data segments, for which it is possible to get a value based on information stored in the system.
Each element consists of the properties that are set in the attribute-based access control.
Only administrator or information security manager can enable the mode to separate system administrator roles.
NOTE. Attribute-base access control structure creation (attribute addition, policy and rules editing) is controlled by the system and it is available to administrator with Changing User Permissions, Distributing Roles, Changing Policy or Change Security Mark and List of Control Access of Any Object privileges.
To use attribute-based access control method:
Select the Use Attribute-Based Access Control checkbox on the Access Control tab of the policies editor.
Create user accounts and groups of users.
Create custom attributes for users, groups of users, objects depending on the formulated task.
Create a set of policies, a policy or rules in the Attribute-Based Access Control section.
Before the user executes a certain operation with an object, the system checks if the operation can be executed through the request. Verification of the execution possibility begins with getting all the attributes, loading sets of policies, policies and rules. After the verification, the values of all the attributes specified in the sets of policies, policies and rules are calculated. The sets of policies are filtered by attribute values, depending on the current request. In the future, only the filtered policies and rules are calculated. As a result of attribute-based access control calculation, a decision will be made to grant access to the user.
IMPORTANT. If no condition is set in attribute-based access control structure, access to all operations with objects is denied.
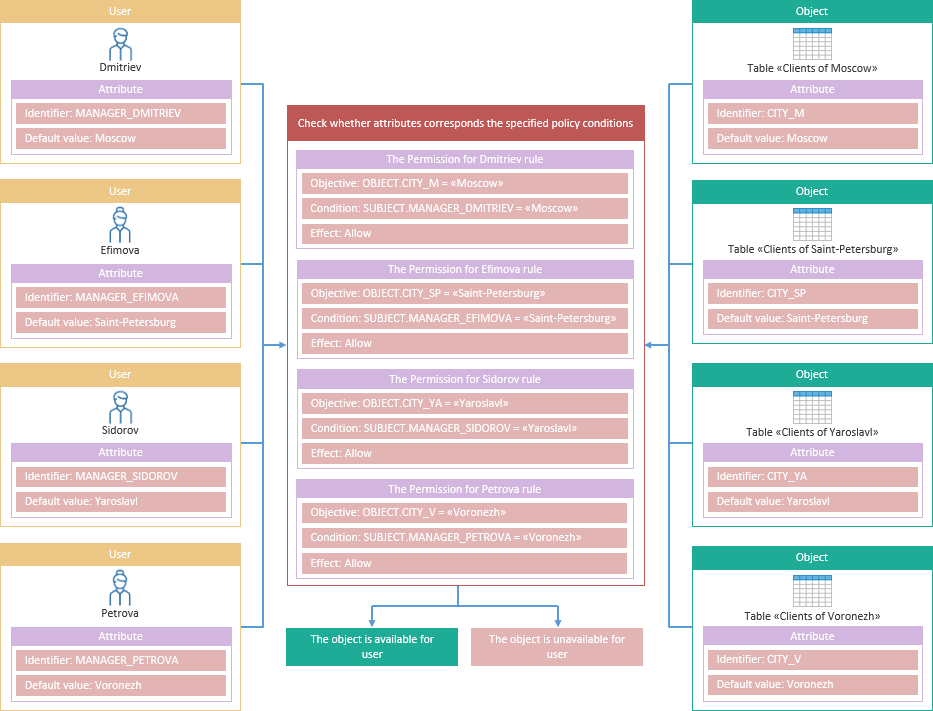
For users who are managers of the company, it is necessary to provide access to customers of their branch.
Managers: Dmitriev, Efimova, Sidorov, Petrova. Branches in the cities: Moscow, St. Petersburg, Yaroslavl, Voronezh.
Show the example execution as a scheme:
Add attributes to users and objects that contains information about customers.
Create a policy with rules in attribute-based access control.

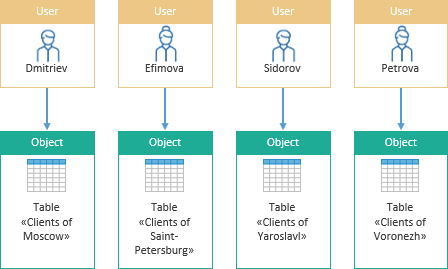
As a result, each manager will be allowed access to the customer table of their branch:
See also:
Selecting Access Control Methods and Their Setup | Adding Access Check Rules and Policies