The below example uses the OpenSSL version for Microsoft Windows OS. It is supposed to use configuration with security server set up to IIS web server. The example shows steps for creating three certificates:
Root certificate is used to sign other certificates.
Server certificate is used by server to check user certificates.
Client certificate is provided by a user to check at server.
The following OpenSSL settings were determined before executing the example:
The dir parameter within the [CA_default] field is changed to C:/iis in the openssl.cnf configuration file.
The C:\iis and C:\iis\newcerts folders are created.
Two files are created in the C:\iis folder: index.txt that is empty, and the serial file without extension that contains 01 value.
A root certificate is required to sign client and server certificates.
To create a root certificate, open OpenSSL and enter the following in the command line:
req -new -x509 -days 1000 -out c:\iis\ca.crt -keyout c:\iis\ca.key -config openssl.cnf
Additional data is requested on executing the command: PEM password and certificate owner data.
TIP. If required, certificate's validity period can be changed in the command or in default OpenSSL settings.
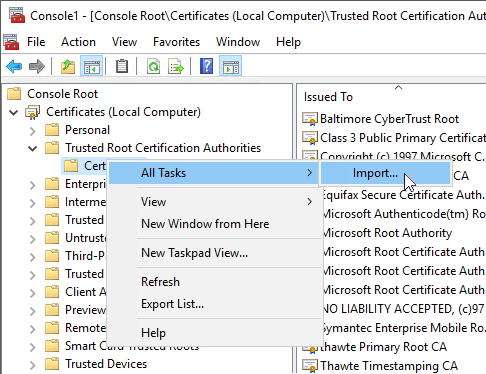
The created certificate must be installed to trusted certification authorities storage:
Open management console (WIN+R) by running the mmc command.
Add (CTRL+M) the certificates snap-in for the local workstation account.
Import the previously created certificate to the Trusted Root Certification Authorities > Certificates folder.

A server certificate is used by IIS web server to check validity of user certificates; to create and sign a server certificate, execute the following steps:
Open a certificate setup page in IIS service manager by clicking the  Server Certificates button.
Server Certificates button.
Select the Create Certificate Request item in the context menu or on the side panel.
Fill in the fields with data about certificate owner.
When it is requested to name the created file, save it in the C:\iis folder as server.csr.
The created request must be signed by means of the root certificate. Open OpenSSL console and execute the command:
ca -days 1000 -policy policy_anything -keyfile c:\iis\ca.key -cert c:\iis\ca.crt -in c:\iis\server.csr -out c:\iis\server.cer -config openssl.cnf
On executing the command it is requested to enter PEM password and answer follow-up questions. After the data is entered, a certificate is created.
The signed server certificate must be installed to IIS web server:
Open a certificate setup page in IIS service manager by clicking the  Server Certificates button.
Server Certificates button.
Select the Request Certificate Install item in the context menu or on the side panel.
Specify the path to the signed certificate: C:\iis\server.cer.
As a result, the signed server certificate is installed to IIS web server.
Open the site page in the IIS service manager, for example, Default Web Site.
Select the Bindings item in the context menu or on the side panel.
Add a new binding: specify https in the Type box, select the previously created server certificate in the drop-down list.
Enable SSL settings for the web site or application in use:
Open a SSL settings setup page in the IIS service manager by clicking the  SSL Settings button.
SSL Settings button.
Select the Require SSL checkbox and the Require Client Certificate radio button.
On two-factor authentication the https protocol is used to connect to web service.
In the settings of user connection to security server specify URL of web service considering the security protocol:
https://<workstation>/fpSS_App_v9.2x64/axis2/services/PP.SOM.SomSec
On using BI server along with security server, set https connection at all steps.
To create a request, open OpenSSL console and execute the command:
req -new -days 1000 -keyout c:\iis\client.key -out c:\iis\client.csr -config openssl.cnf
On executing the command it is suggested to set PEM password and additional data about certificate owner.
After the data is entered, a key and a request for client certificate are created.
The created request must be signed by means of the root certificate. Open OpenSSL console and execute the command:
ca -days 1000 -policy policy_anything -keyfile c:\iis\ca.key -cert c:\iis\ca.crt -in c:\iis\client.csr -out c:\iis\client.cer -config openssl.cnf
On executing the command it is requested to enter PEM password and answer follow-up questions. After the data is entered, a certificate is created.
To import a certificate to certificate storage with the key, convert the certificate with the key into a *.pfx. container.
Execute the command in OpenSSL console:
pkcs12 -export -inkey c:\iis\client.key -in c:\iis\client.crt -out c:\iis\client.pfx
On executing the command it is requested to enter PEM password.
After a container is created, pass it to the client workstation and import to the certificate storage.
A certificate is bound to the particular user on the General Properties tab in user properties.
Select the From File item in the drop-down menu of the Add button and specify the created client certificate.
As a result, the user is allowed access to repository only on presenting the user certificate.
Before checking certificate performance restart IIS web server.
To check if certificate requests work, check access to security server web service. Open the URL in the browser:
https://<workstation>/fpSS_App_v9.2x64/axis2/services
If everything is set correctly, a dialog box for selecting a certificate for site authentication opens.
If the certificate is correctly set, a page with available web service operations is displayed.
See also:
Setting Up Two-Factor Authentication | Example of Setting Up Two-Factor Authentication on Linux