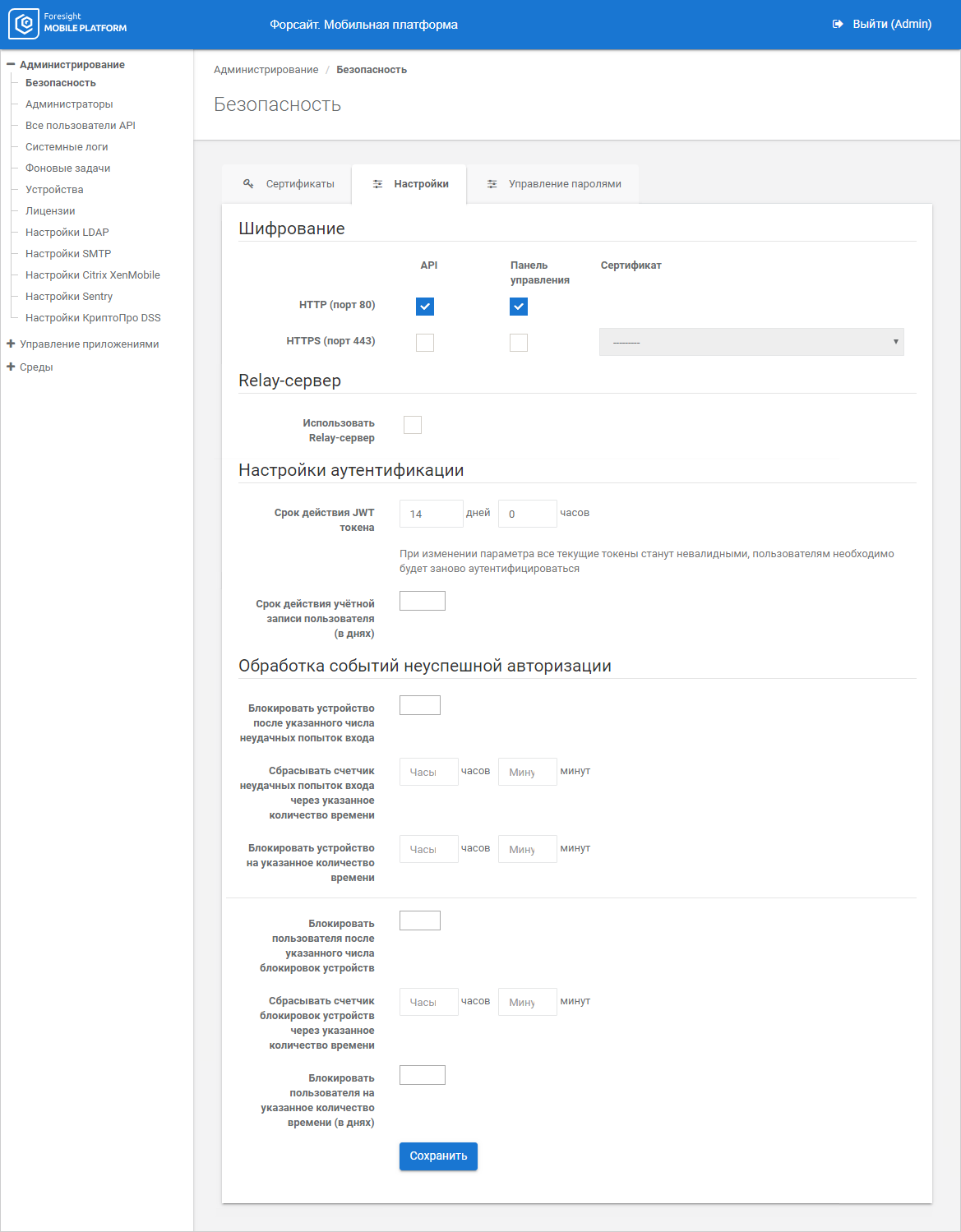
To set up security parameters, go to the Settings tab in the Security subsection:

To set encryption, select the API, Control Panel checkboxes next to the protocols:
HTTP (port 80). Unencrypted protocol.
NOTE. HTTP protocol is used by default.
HTTPS (port 443). Protocol with encryption certificate. When HTTPS protocol is used, also select the added encryption certificate to provide TLS session in the Certificate box. The certificate is issued for the server name <myserver.russia.ru>.
After executing the operations traffic encryption is set.
To use Relay server, select the Use Relay Server checkbox.
Relay server is a server, at which Relay service is deployed. Relay service enables the user to establish a connection between a mobile device and mobile platform server on heightened requirements to protection of internal corporate network data. In this case DMZ ports into internal network are closed, only ports from internal network into external network are opened.
To set Relay server, see the Installing Relay Server section.
Connection with the Relay server is established on the mobile platform server side. The Relay service enables the user to accept request from mobile platform server to establish connection. The established connection is used to redirect requests from mobile client to mobile platform server.
NOTE. When Relay server is used, interaction between mobile client and mobile platform server is slowed down.
The scheme of interaction between mobile client, Relay server, and mobile platform server:
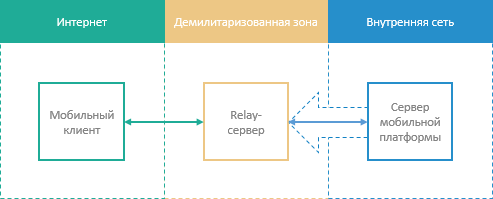
The mobile platform server establishes connection with the Relay server.
The mobile client exchanges data with the mobile platform server using the Relay server located in DMZ.
The Relay server interacts with the mobile client and mobile platform server:
If receives request to establish connection with the mobile platform server.
It exchanges requests with the mobile client.
It redirects the requests directed to the internal network to the mobile platform server within the established connection.
It prohibits connection if the connection request is directed not from the mobile platform server.
To use Relay server, fill in the boxes:
Relay server URL. Enter Relay server name to provide a request to establish connection from mobile platform server. The box is mandatory.
Port. Specify port number in the numeric format. By default, the 8022 port is used on installing Relay server. The box is mandatory.
The Relay server is addressed from the mobile client after the connection is established on the mobile platform server side via the 10080 (http) or 10443 (https) port.
When the user is authenticated at mobile platform server, a user token is generated. The token is valid through 14 days by default.
To change JWT token validity, set the validity next to the JWT Validity parameter.
NOTE. When token validity is changed, all current tokens are invalid, the users must repeat authentication.
To set validity of all user accounts, enter the number of days in the User Account Validity (Days) box. By default, validity is not set, accounts are not limited in time.
To set validity for a specific API user, use the Account Validity box in API user parameters. If validity is set for a specific API user, the specified user account validity is ignored in authentication settings.
To handle API user failures, determine the parameters:
Lock device after the specified number of failed logins.
Reset counter of failed logins in the specified time.
Lock device during the specified time.
Lock user after the specified number of device locks.
Reset counter of device locks in the specified time.
Lock user during the specified time (days).
If the specified number of authorization failures for the specific time period is exceeded, the mobile device is locked for the specified period. When the mobile device is locked, API user cannot be authorized on this device. If the number of mobile device locks for the specific time period is exceeded, API user is locked for the specified period. When the specified parameters of authorization failure handling are changed for locked API users, locking time is recalculated.
When API user is locked, the Locked for Security Reasons checkbox is automatically selected, and the message "Locked until <Date>" is displayed in specific API user parameters. When API user is locked, authorization is disabled, user session is interrupted on all mobile devices.
To unlock API user, deselect the Locked for Security Reasons checkbox or wait until the end of the specified user lock period.
See also: