Attribute-based access control method allows for setting access permissions for specific elements of table MDM dictionary only on parallel using with discretionary access control method enumeration.
The attribute element is set as OBJECT.ELEMENT.<attribute identifier>. Attribute identifiers are contained on the Attributes tab on opening dictionary for edit.
NOTE. An element attribute is set only in additional condition of the rule. On creating an additional condition, take into account features of attribute use.
Operations with MDM dictionary elements are contained in the DictionarySpecificRights.
To apply access permissions restriction to MDM dictionary elements, see the Access Permissions for MDM Repository Objects section.
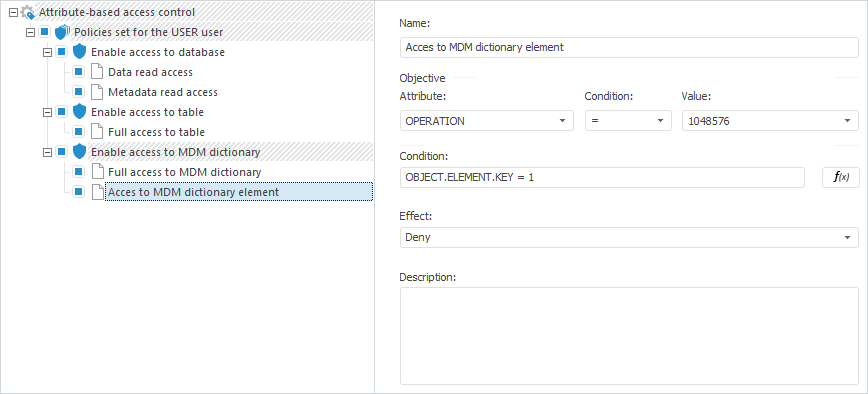
Consider an example of denying user access to read the table MDM dictionary element with the 1 key.
Executing the example requires the following conditions to be satisfied:
The repository root contains a table MDM dictionary with the DICTIONARY identifier. The dictionary must contain at least two elements.
The security manager contains the USER user.
checkboxes in the Policy Editor security manager section, theUse Attribute-Based Access Control, Use Discretionary Access Control checkboxes are selected and the OR access permissions combination algorithm is selected.
Discretionary access control parameters for a specific user enables all operations with objects:
Folder containing MDM dictionary. If MDM dictionary is not located in the repository root, but in the folder or folder hierarchy, each folder must not have forbidden operations.
Database that stores MDM dictionary data.
Internal MDM dictionary table.
Discretionary access control permissions are set up for each object on the Discretionary Access Control tab in the Access Control Settings dialog box.
Add links to the ABAC, Metabase, Rds, ForeSystem (for Fore.NET example) system assemblies.
Sub UserProc;
Var
PolicyObject: IABACRootPolicyObject;
PolicySet: IABACPolicySet;
Policy: IABACPolicy;
Rules: IABACRules;
Rule: IABACRule;
MB: IMetabase;
MS: IMetabaseSecurity;
Lic: Object;
DimObj: IMetabaseObject;
Dim: IRdsDictionary;
Begin
MB := MetabaseClass.Active;
//Get license to work with security manager
Lic := MB.RequestLicense(UiLicenseFeatureType.Adm);
MS := MB.Security;
// Set the Elements Have Attribute Access Permissions attribute for table MDM dictionary
DimObj := MB.ItemById("DICTIONARY").Edit;
Dim := DimObj As IRdsDictionary;
Dim.AbacSecured := True;
DimObj.Save;
// Get attribute-based access control structure
PolicyObject := MB.Security.Policy.ABACRules;
// Clear attribute-based access control structure and set a new one
PolicyObject.Policies.Clear;
// Set algorithm of root policy of attribute-based access control - allow overriding
PolicyObject.CombineAlgorithm := ABACCombineAlgorithm.PermitOverride;
// Add a policies set
PolicySet := PolicyObject.Policies.Add;
PolicySet.Name(MB.CurrentLocale) := "Policies set for the USER user";
PolicySet.Target.AttributeId := "SUBJECT.NAME";
PolicySet.Target.Operation := ABACTargetOperation.Equal;
PolicySet.Target.AttributeValue := "USER";
PolicySet.CombineAlgorithm := ABACCombineAlgorithm.PermitOverride;
// Add a policy to access table MDM dictionary with the DICTIONARY identifier
Policy := PolicySet.Policies.Add;
Policy.Name(MB.CurrentLocale) := "Allow access to MDM dictionary";
Policy.Target.AttributeId := "OBJECT.ID";
Policy.Target.Operation := ABACTargetOperation.Equal;
Policy.Target.AttributeValue := "DICTIONARY";
Policy.CombineAlgorithm := ABACCombineAlgorithm.PermitOverride;
// Add a rule to deny access element of MDM dictionary with the 1 key
Rules := Policy.Rules;
Rule := Rules.Add;
Rule.Name(LocaleCodeID.Russian) := "Deny access to MDM dictionary element";
Rule.Target.AttributeId := "OPERATION";
Rule.Target.Operation := ABACTargetOperation.Equal;
Rule.Target.AttributeValue := 1048576;
Rule.Condition.AsString := "OBJECT.ELEMENT.KEY = 1";
Rule.Effect := ABACRuleEffect.Deny;
// Apply changes in security manager
MS.Apply;
// Check in license
Lic := Null;
End Sub UserProc;
Imports Prognoz.Platform.Interop.ABAC;
Imports Prognoz.Platform.Interop.Metabase;
Imports Prognoz.Platform.Interop.Rds;
Imports Prognoz.Platform.Interop.ForeSystem;
…
Public Shared Sub Main(Params: StartParams);
Var
PolicyObject: IABACRootPolicyObject;
PolicySet: IABACPolicySet;
Policy: IABACPolicy;
Rules: IABACRules;
Rule: IABACRule;
MB: IMetabase;
MS: IMetabaseSecurity;
Lic: Object;
DimObj: IMetabaseObject;
Dim: IRdsDictionary;
Begin
MB := Params.Metabase;
//Get license to work with security manager
Lic := MB.RequestLicense(UiLicenseFeatureType.lftAdm);
MS := MB.Security;
// Set the Elements Have Attribute Access Permissions attribute for MDM dictionary
DimObj := MB.ItemById["DICTIONARY"].Edit();
Dim := DimObj As IRdsDictionary;
Dim.AbacSecured := True;
DimObj.Save();
// Get attribute-based access control structure
PolicyObject := MB.Security.Policy.ABACRules;
// Clear attribute-based access control structure and set a new one
PolicyObject.Policies.Clear;
// Set algorithm of root policy of attribute-based access control - allow overriding
PolicyObject.CombineAlgorithm := ABACCombineAlgorithm.abacrcaPermitOverride;
// Add a policies set
PolicySet := PolicyObject.Policies.Add();
PolicySet.Name[MB.CurrentLocale] := "Policies set for the USER user";
PolicySet.Target.AttributeId := "SUBJECT.NAME";
PolicySet.Target.Operation := ABACTargetOperation.abactoEqual;
PolicySet.Target.AttributeValue := "USER";
PolicySet.CombineAlgorithm := ABACCombineAlgorithm.abacrcaPermitOverride;
// Add a policy to access table MDM dictionary with the DICTIONARY identifier
Policy := PolicySet.Policies.Add();
Policy.Name[MB.CurrentLocale] := "Allow access to MDM dictionary";
Policy.Target.AttributeId := "OBJECT.ID";
Policy.Target.Operation := ABACTargetOperation.abactoEqual;
Policy.Target.AttributeValue := "DICTIONARY";
Policy.CombineAlgorithm := ABACCombineAlgorithm.abacrcaPermitOverride;
// Add a rule to deny access element of MDM dictionary with the 1 key
Rules := Policy.Rules;
Rule := Rules.Add();
Rule.Name[MB.CurrentLocale] := "Deny access to MDM dictionary element";
Rule.Target.AttributeId := "OPERATION";
Rule.Target.Operation := ABACTargetOperation.abactoEqual;
Rule.Target.AttributeValue := 1048576;
Rule.Condition.AsString := "OBJECT.ELEMENT.KEY = 1";
Rule.Effect := ABACRuleEffect.abacreDeny;
// Apply changes in security manager
MS.Apply();
// Check in license
Lic := Null;
End Sub;
After executing the example:
In basic settings of table MDM dictionary theElements have Attribute-Based Access Permissions checkbox will be selected.
In the Attribute-Based Access Controlof security manager the specified attribute-based access control structure is added with denial of user access to read the MDM dictionary element with the 1 key:

When the attribute-based access control is implemented in the object navigator, the MDM dictionary element with the 1 key is not displayed for the USER user.
See also:
Examples | Access Permissions for MDM Repository Objects | Basic Dictionary Settings