System Configurations and Their Working Principles
Foresight Analytics Platform can work in various configurations by using separate servers to focus on business logic core, security core or user interface.
See below basic configurations. In order to increase fault tolerance in each configuration can implement BI servers cluster.
Conventions
The configurations given below use the following legend:

|
Business logic core provides work logic of Foresight Analytics Platform, logic of interaction between objects, loads, processes, calculates and saves data. |

|
Security core executes administration functions and information security functions. |

|
User interface ensures interaction of the user with Foresight Analytics Platform. |

|
Web service is used to interact between the web application and system servers via http/https requests. |

|
Interaction between configuration elements on the level of Foresight Analytics Platform. |

|
Interaction between configuration elements on user level in manual mode. |
Standard Configuration
Standard configuration of Foresight Analytics Platform includes the use of the desktop and web applications:
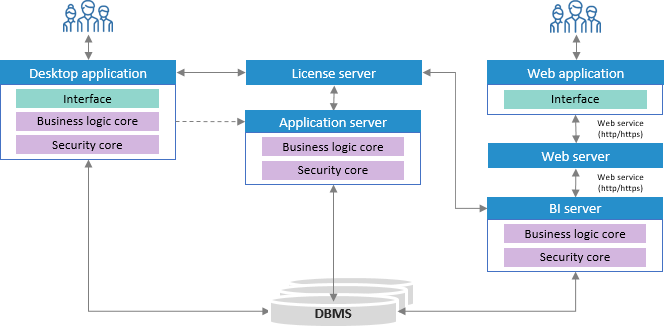
On using the desktop application:
A user interacts with desktop application interface.
The desktop application sends requests to license server, as a result the desktop application determines access to the functionality.
The desktop application interacts with database via the DBMS driver using business logic core.
If the web application is used, business logic and security functions are performed by BI server, the user interface is presented by the web application:
The user interacts with web application interface.
The web application interacts with web server and BI server via the PP.SOM.Som access point. The scheme shows general interaction, a detailed scheme is given in the Installing and Setting Up Web Application Back End section.
BI server sends requests to license server, as a result BI server determines access to the functionality.
The BI server interacts with database via the DBMS driver using business logic core.
When executing scheduled resource-intensive tasks:
The user sets up scheduled tasks in the desktop application, sends the settings to the application server and starts theTask Scheduler tool.
Application server sends requests to license server, as a result application server determines access to the functionality.
The application server executes scheduled resource-intensive tasks and interacts with database via the DBMS driver using business logic core.
BI server and web application installation is described in the articles: Installing Web Application on Windows OS and Installing Web Application on Linux OS.
Configuration with Security Server
Security core functions can be moved to security server:
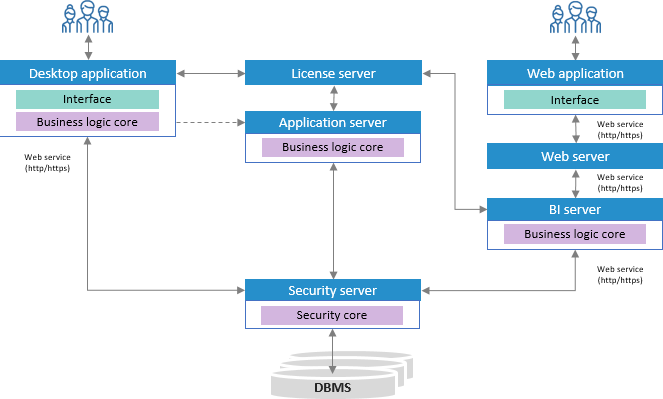
On using the desktop application:
A user interacts with desktop application interface.
The desktop application sends requests to license server, as a result the desktop application determines access to the functionality.
Desktop application via the PP.SOM.SomSec access point interacts with security server.
The security server sends a request via DBMS driver, gets data and returns it to the business logic core.
If the web application is used, business logic function is performed by BI server, the user interface is presented by the web application:
A user interacts with web application interface.
The web application interacts with web server and BI server via the PP.SOM.Som access point. The scheme shows general interaction, a detailed scheme is given in the Installing and Setting Up Web Application Back End section.
BI server sends requests to license server, as a result BI server determines access to the functionality.
BI server interacts with security server via the PP.SOM.SomSec access point.
The security server interacts:
When executing scheduled resource-intensive tasks:
The user sets up scheduled tasks in the desktop application, sends the settings to the application server and starts theTask Scheduler tool.
Application server sends requests to license server, as a result application server determines access to the functionality.
The application server via the access point PP.SOM.SomSec interacts with the security server.
The security server sends a request via DBMS driver, gets data and returns it to the business logic core.
The application server executes scheduled resource-intensive tasks.
BI server and web application installation is described in the articles: Installing Web Application on Windows OS and Installing Web Application on Linux OS.







